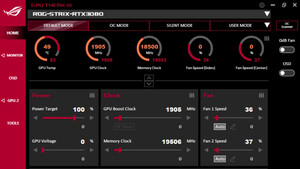
hi,
ich versuche mich am übertakten und veränder dementsprechend die vcore der cpu schrittweise. meistens bekomme ich dann bei zu wenig den 0x124er bluescreen, was sich aber dann mit mehr vcore wieder gibt.
nun hab ich auch ein paar mal andere nummern gehabt, gerade z.B den 0x24 (zuvor auch: 0x3B, 0x1E und 0x1A):
-> es scheint wohl irgendwas mit everest zu tun haben? kann es sein, dass sich das tool in diesem fall nicht wirklich zur systemüberwachung eignet oder gibt es doch andere gründe?
...den RAM habe ich übrigens nicht übertaktet (unlinked.. -> sysinfo siehe sig)
danke schonmal für anregungen
ich versuche mich am übertakten und veränder dementsprechend die vcore der cpu schrittweise. meistens bekomme ich dann bei zu wenig den 0x124er bluescreen, was sich aber dann mit mehr vcore wieder gibt.
nun hab ich auch ein paar mal andere nummern gehabt, gerade z.B den 0x24 (zuvor auch: 0x3B, 0x1E und 0x1A):
Loading Dump File [C:\Windows\Minidump\081312-16863-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*C:\symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 7601.17835.amd64fre.win7sp1_gdr.120503-2030
Machine Name:
Kernel base = 0xfffff800`02c50000 PsLoadedModuleList = 0xfffff800`02e94670
Debug session time: Mon Aug 13 01:54:09.503 2012 (UTC + 2:00)
System Uptime: 0 days 0:06:21.939
Loading Kernel Symbols
...............................................................
................................................................
...........................
Loading User Symbols
Loading unloaded module list
....
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 24, {1904fb, fffff8800a45db48, fffff8800a45d3a0, fffff80002fc7256}
Probably caused by : ntkrnlmp.exe ( nt!CcMapData+96 )
Followup: MachineOwner
---------
2: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
NTFS_FILE_SYSTEM (24)
If you see NtfsExceptionFilter on the stack then the 2nd and 3rd
parameters are the exception record and context record. Do a .cxr
on the 3rd parameter and then kb to obtain a more informative stack
trace.
Arguments:
Arg1: 00000000001904fb
Arg2: fffff8800a45db48
Arg3: fffff8800a45d3a0
Arg4: fffff80002fc7256
Debugging Details:
------------------
EXCEPTION_RECORD: fffff8800a45db48 -- (.exr 0xfffff8800a45db48)
ExceptionAddress: fffff80002fc7256 (nt!CcMapData+0x0000000000000096)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 0000000000000000
Parameter[1]: ffffffffffffffff
Attempt to read from address ffffffffffffffff
CONTEXT: fffff8800a45d3a0 -- (.cxr 0xfffff8800a45d3a0)
rax=00019d690cda3ad3 rbx=000000000000000e rcx=0000000000000007
rdx=0000000000000001 rsi=fffff8800a45e340 rdi=fffffa800718e140
rip=fffff80002fc7256 rsp=fffff8800a45dd80 rbp=0000000000000090
r8=0000000000000400 r9=0000000000000000 r10=0000000000000000
r11=0000000000000001 r12=0000000000000001 r13=fffffa800511fd80
r14=fffff8800a45de88 r15=0000000000000001
iopl=0 nv up ei pl zr na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00010246
nt!CcMapData+0x96:
fffff800`02fc7256 488b4808 mov rcx,qword ptr [rax+8] ds:002b:00019d69`0cda3adb=????????????????
Resetting default scope
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN7_DRIVER_FAULT
PROCESS_NAME: everest.exe
CURRENT_IRQL: 0
ERROR_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced memory at 0x%08lx. The memory could not be %s.
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced memory at 0x%08lx. The memory could not be %s.
EXCEPTION_PARAMETER1: 0000000000000000
EXCEPTION_PARAMETER2: ffffffffffffffff
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff80002efe100
GetUlongFromAddress: unable to read from fffff80002efe1c0
ffffffffffffffff
FOLLOWUP_IP:
nt!CcMapData+96
fffff800`02fc7256 488b4808 mov rcx,qword ptr [rax+8]
FAULTING_IP:
nt!CcMapData+96
fffff800`02fc7256 488b4808 mov rcx,qword ptr [rax+8]
BUGCHECK_STR: 0x24
LAST_CONTROL_TRANSFER: from fffff880012f41e2 to fffff80002fc7256
STACK_TEXT:
fffff880`0a45dd80 fffff880`012f41e2 : fffff8a0`03e4c3a8 fffff8a0`03e34010 00000000`0000035a fffff880`0000000e : nt!CcMapData+0x96
fffff880`0a45de40 fffff880`012efd5c : fffff880`0a45e340 fffffa80`05109180 fffff8a0`023d7018 fffff8a0`0a125801 : Ntfs!NtfsReadMftRecord+0xb2
fffff880`0a45def0 fffff880`012f4ae0 : fffff880`0a45e290 fffff8a0`023d71f0 fffff8a0`023d7140 fffff880`0a45e120 : Ntfs!NtfsLookupInFileRecord+0x6c
fffff880`0a45df80 fffff880`012f8db1 : fffff880`0a45e340 fffff880`012ef166 00000000`0078000e fffff8a0`0a125820 : Ntfs!FindFirstIndexEntry+0x50
fffff880`0a45e010 fffff880`012eccf5 : fffff880`0a45e340 fffff880`0a45e340 fffff8a0`0bef9001 00000000`00000000 : Ntfs!NtfsFindIndexEntry+0x5d
fffff880`0a45e080 fffff880`012ce441 : fffff880`0a45e340 fffffa80`048a6010 fffff880`0a45e290 fffffa80`048a6000 : Ntfs!NtfsCommonCreate+0x7c5
fffff880`0a45e260 fffff880`00e01367 : fffffa80`048a6010 fffffa80`048a63b0 fffff880`0a45e5d0 fffffa80`04573a00 : Ntfs!NtfsNetworkOpenCreate+0x115
fffff880`0a45e540 fffff880`00e22aed : 00000000`00000000 fffffa80`048a63b0 00000000`0000000b 00000000`0000000b : fltmgr!FltpPerformFastIoCall+0x357
fffff880`0a45e5a0 fffff800`02fc9118 : 00000000`00000045 fffff880`0a45e9e0 fffffa80`00000080 00000000`000007ff : fltmgr!FltpFastIoQueryOpen+0x15d
fffff880`0a45e640 fffff800`02fc5488 : fffffa80`044fca50 fffff800`00000000 fffffa80`0420b690 fffff880`00000001 : nt!IopParseDevice+0xad8
fffff880`0a45e7d0 fffff800`02fc66a6 : 00000000`00000000 fffffa80`0420b690 00000000`00000000 fffffa80`039dff30 : nt!ObpLookupObjectName+0x588
fffff880`0a45e8c0 fffff800`02fa65c6 : fffff880`0a45ea10 00000000`0008e308 fffff880`0a45ea01 fffffa80`048368f8 : nt!ObOpenObjectByName+0x306
fffff880`0a45e990 fffff800`02cce453 : fffffa80`0718e140 00000000`00000000 fffffa80`0718e140 fffffa80`071b4de0 : nt!NtQueryAttributesFile+0x145
fffff880`0a45ec20 00000000`775916ea : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`0008e2c8 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x775916ea
SYMBOL_STACK_INDEX: 0
SYMBOL_NAME: nt!CcMapData+96
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
DEBUG_FLR_IMAGE_TIMESTAMP: 4fa390f3
STACK_COMMAND: .cxr 0xfffff8800a45d3a0 ; kb
FAILURE_BUCKET_ID: X64_0x24_nt!CcMapData+96
BUCKET_ID: X64_0x24_nt!CcMapData+96
Followup: MachineOwner
---------
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*C:\symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 7601.17835.amd64fre.win7sp1_gdr.120503-2030
Machine Name:
Kernel base = 0xfffff800`02c50000 PsLoadedModuleList = 0xfffff800`02e94670
Debug session time: Mon Aug 13 01:54:09.503 2012 (UTC + 2:00)
System Uptime: 0 days 0:06:21.939
Loading Kernel Symbols
...............................................................
................................................................
...........................
Loading User Symbols
Loading unloaded module list
....
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 24, {1904fb, fffff8800a45db48, fffff8800a45d3a0, fffff80002fc7256}
Probably caused by : ntkrnlmp.exe ( nt!CcMapData+96 )
Followup: MachineOwner
---------
2: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
NTFS_FILE_SYSTEM (24)
If you see NtfsExceptionFilter on the stack then the 2nd and 3rd
parameters are the exception record and context record. Do a .cxr
on the 3rd parameter and then kb to obtain a more informative stack
trace.
Arguments:
Arg1: 00000000001904fb
Arg2: fffff8800a45db48
Arg3: fffff8800a45d3a0
Arg4: fffff80002fc7256
Debugging Details:
------------------
EXCEPTION_RECORD: fffff8800a45db48 -- (.exr 0xfffff8800a45db48)
ExceptionAddress: fffff80002fc7256 (nt!CcMapData+0x0000000000000096)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 0000000000000000
Parameter[1]: ffffffffffffffff
Attempt to read from address ffffffffffffffff
CONTEXT: fffff8800a45d3a0 -- (.cxr 0xfffff8800a45d3a0)
rax=00019d690cda3ad3 rbx=000000000000000e rcx=0000000000000007
rdx=0000000000000001 rsi=fffff8800a45e340 rdi=fffffa800718e140
rip=fffff80002fc7256 rsp=fffff8800a45dd80 rbp=0000000000000090
r8=0000000000000400 r9=0000000000000000 r10=0000000000000000
r11=0000000000000001 r12=0000000000000001 r13=fffffa800511fd80
r14=fffff8800a45de88 r15=0000000000000001
iopl=0 nv up ei pl zr na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00010246
nt!CcMapData+0x96:
fffff800`02fc7256 488b4808 mov rcx,qword ptr [rax+8] ds:002b:00019d69`0cda3adb=????????????????
Resetting default scope
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN7_DRIVER_FAULT
PROCESS_NAME: everest.exe
CURRENT_IRQL: 0
ERROR_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced memory at 0x%08lx. The memory could not be %s.
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - The instruction at 0x%08lx referenced memory at 0x%08lx. The memory could not be %s.
EXCEPTION_PARAMETER1: 0000000000000000
EXCEPTION_PARAMETER2: ffffffffffffffff
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff80002efe100
GetUlongFromAddress: unable to read from fffff80002efe1c0
ffffffffffffffff
FOLLOWUP_IP:
nt!CcMapData+96
fffff800`02fc7256 488b4808 mov rcx,qword ptr [rax+8]
FAULTING_IP:
nt!CcMapData+96
fffff800`02fc7256 488b4808 mov rcx,qword ptr [rax+8]
BUGCHECK_STR: 0x24
LAST_CONTROL_TRANSFER: from fffff880012f41e2 to fffff80002fc7256
STACK_TEXT:
fffff880`0a45dd80 fffff880`012f41e2 : fffff8a0`03e4c3a8 fffff8a0`03e34010 00000000`0000035a fffff880`0000000e : nt!CcMapData+0x96
fffff880`0a45de40 fffff880`012efd5c : fffff880`0a45e340 fffffa80`05109180 fffff8a0`023d7018 fffff8a0`0a125801 : Ntfs!NtfsReadMftRecord+0xb2
fffff880`0a45def0 fffff880`012f4ae0 : fffff880`0a45e290 fffff8a0`023d71f0 fffff8a0`023d7140 fffff880`0a45e120 : Ntfs!NtfsLookupInFileRecord+0x6c
fffff880`0a45df80 fffff880`012f8db1 : fffff880`0a45e340 fffff880`012ef166 00000000`0078000e fffff8a0`0a125820 : Ntfs!FindFirstIndexEntry+0x50
fffff880`0a45e010 fffff880`012eccf5 : fffff880`0a45e340 fffff880`0a45e340 fffff8a0`0bef9001 00000000`00000000 : Ntfs!NtfsFindIndexEntry+0x5d
fffff880`0a45e080 fffff880`012ce441 : fffff880`0a45e340 fffffa80`048a6010 fffff880`0a45e290 fffffa80`048a6000 : Ntfs!NtfsCommonCreate+0x7c5
fffff880`0a45e260 fffff880`00e01367 : fffffa80`048a6010 fffffa80`048a63b0 fffff880`0a45e5d0 fffffa80`04573a00 : Ntfs!NtfsNetworkOpenCreate+0x115
fffff880`0a45e540 fffff880`00e22aed : 00000000`00000000 fffffa80`048a63b0 00000000`0000000b 00000000`0000000b : fltmgr!FltpPerformFastIoCall+0x357
fffff880`0a45e5a0 fffff800`02fc9118 : 00000000`00000045 fffff880`0a45e9e0 fffffa80`00000080 00000000`000007ff : fltmgr!FltpFastIoQueryOpen+0x15d
fffff880`0a45e640 fffff800`02fc5488 : fffffa80`044fca50 fffff800`00000000 fffffa80`0420b690 fffff880`00000001 : nt!IopParseDevice+0xad8
fffff880`0a45e7d0 fffff800`02fc66a6 : 00000000`00000000 fffffa80`0420b690 00000000`00000000 fffffa80`039dff30 : nt!ObpLookupObjectName+0x588
fffff880`0a45e8c0 fffff800`02fa65c6 : fffff880`0a45ea10 00000000`0008e308 fffff880`0a45ea01 fffffa80`048368f8 : nt!ObOpenObjectByName+0x306
fffff880`0a45e990 fffff800`02cce453 : fffffa80`0718e140 00000000`00000000 fffffa80`0718e140 fffffa80`071b4de0 : nt!NtQueryAttributesFile+0x145
fffff880`0a45ec20 00000000`775916ea : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`0008e2c8 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x775916ea
SYMBOL_STACK_INDEX: 0
SYMBOL_NAME: nt!CcMapData+96
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
DEBUG_FLR_IMAGE_TIMESTAMP: 4fa390f3
STACK_COMMAND: .cxr 0xfffff8800a45d3a0 ; kb
FAILURE_BUCKET_ID: X64_0x24_nt!CcMapData+96
BUCKET_ID: X64_0x24_nt!CcMapData+96
Followup: MachineOwner
---------
...den RAM habe ich übrigens nicht übertaktet (unlinked.. -> sysinfo siehe sig)
danke schonmal für anregungen