Hallo,
vor Kurzem habe ich mein Win XP durch Win XP 64bit ersetzt. Beim Installieren der Hardware + Treiber, Software usw. hab ich dann irgendwann einen Bluescreen erhalten. Seither habe ich ihn alle 2-3 Startvorgänge, meistens kurz vor oder nach der Benutzeranmeldung, gelegentlich auch, wenn das System gerade komplett hochgefahren ist.
Es handelt sich immer wieder um einen der folgenden Fehler:
0x24 irgendwas mit ntfs.sys
0x19 BAD_POOL_HEADER
0xC2 BAD_POOL_CALLER
0x3B SYSTEM_SERVICE_EXEPTION
0x0A IRQL_NOT_LESS_OR_EQUAL
0xD6 cmdguard.sys The driver is attemting to access memory beyond the end of the allocation
Während des Betriebes ruckelt das System manchmal etwas, nicht mal unbedingt bei großen Anwendungen. Z.B. Firefox sorgt hin und wieder für 100% CPU Auslastung bei einen der beiden Prozessorkerne. Z.B. wenn ich ein neues Lesezeichen hinzufügen möchte, dann geht fast nix mehr.
Systemdaten:
Athlon 64 X2 Dual Core 6000+
Asus M2N SLI-Deluxe
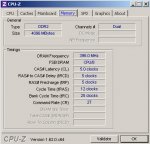
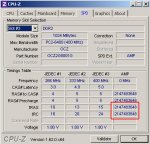
4x 1GB OCZ PC6400
Ich habe viel im Netz gesucht, doch man findet zu jeder Fehlermeldung nahezu jede mögliche Fehlerursache als Erklärung, was im Endeffekt leider nicht weiter führt. Irgendwann bin ich dann über das Debugging Tool und die Crash Dumps gestolpert und habe versucht, mich da einzuarbeiten. Leider ist das aber so komplex, dass ich da nicht weiter komme.
Jedenfalls klang es für mich immer wieder so, als würde Information im Arbeitsspeicher verloren gehen, nicht zuletzt wegen dem zuletzt aufgelisteten Fehler 0xD6.
Ich habe dann Memtest laufen lassen. Komischerweise prüft Memtest zunächst 0 - 2048 MB, dann aber 2048 - 3583 MB und anschließend noch 4096 - 4608 MB? Da kann doch was nicht stimmen?
Es werden aber keine Fehler gefunden, auch nach Stunden nicht.
Wenn ich unter configuration den Arbeitsspeicher erkennen lasse, dann zeigt Memtest nur 3838 MB an und hängt sich nach wenigen Sekunden komplett auf.
Ich habe dann jeden Speicher einzeln getestet, keine Fehler, das System läuft auch.
Bestätigt wird das Ganze durch diesen Arbeitsspeichertest von Microsoft auf der Ultimate Boot Disk. Da bekam ich eine Meldung die in etwa so lautete: Ein Teil des Arbeitsspeichers kann nicht überprüft werden, da er außerhalb des gültigen Bereiches liegt (müsste ich nochmal genau nachschauen).
(Erwähnenswert in dem Zusammenhang sei noch, dass unter dem alten Win XP eine Festplatte mit 500GB zuletzt mit 2048GB angezeigt wurde. Eine zweite 500GB Platte wurde teilweise richtig angezeigt, teilweise aber auch mit 2048GB. Beide Platten sind aktuell NICHT verbaut.)
Mein Gedanke ist aktuell, dass vllt das Board einen Fehler hat? Worüber läuft denn die Ansteuerung der RAMs?
Dann habe ich gelesen, dass man über Start -Ausführen - sfc /scannow die Systemdateien überprüfen kann. Das habe ich gemacht, seither sind die Bluescreens etwas seltener geworden (alle 10-15 Startvorgänge), aber das hängende System bleibt.
Als nächstes habe ich mir den Verifier angeschaut. Hier habe ich mal alle möglichen Überprüfungen laufen lassen, werde aber aus den Ergebnissen nicht wirklich schlau.
Jedenfalls kamen mir 3 Dinge komisch vor:
1. Bei "Erfolgreiche Poolzuweisung ohne Kennung" steht 1
2. Wenn ich die Datenträger-Integritätüberprüfung aktiviere, bekomme ich beim Hochfahren immer folgenden Bluescreen: IO system verification error in crcdisk.sys (WDM Driver Error 226) [crcdisk.sys+1a70 at FFFFFADF90CSCA70]
3. Wenn ich die erweiterte E/A Prüfung aktiviere, bekomme ich immer einen der folgenden beiden Bluescreens:
- 0x35 no_more_IRP_stack_locations
- 0x50 page_fault_in_nonpaged_area
Kann mir jemand sagen, was das alles bedeuten könnte?
Schließlich habe ich noch WhoCrashed laufen lassen. Da steht allerdings überall nur, dass es ein Treiberfehler ist. Auch bei dem Debugging Tool von MS erhalte ich immer wieder Hinweise auf Treiber. Jedoch sind es immer wieder andere Treiber. Und es sind ja vermutlich nicht mehrere beschädigt.
Ich hoffe, dass mir hier jemand weiterhelfen kann. So langsam weiß ich nicht mehr, was ich machen soll...
Im folgenden Beitrag noch ein paar Ergebnisse vom Debugging Tool und WhoCrashed, vllt kann jemand was damit anfangen.
vor Kurzem habe ich mein Win XP durch Win XP 64bit ersetzt. Beim Installieren der Hardware + Treiber, Software usw. hab ich dann irgendwann einen Bluescreen erhalten. Seither habe ich ihn alle 2-3 Startvorgänge, meistens kurz vor oder nach der Benutzeranmeldung, gelegentlich auch, wenn das System gerade komplett hochgefahren ist.
Es handelt sich immer wieder um einen der folgenden Fehler:
0x24 irgendwas mit ntfs.sys
0x19 BAD_POOL_HEADER
0xC2 BAD_POOL_CALLER
0x3B SYSTEM_SERVICE_EXEPTION
0x0A IRQL_NOT_LESS_OR_EQUAL
0xD6 cmdguard.sys The driver is attemting to access memory beyond the end of the allocation
Während des Betriebes ruckelt das System manchmal etwas, nicht mal unbedingt bei großen Anwendungen. Z.B. Firefox sorgt hin und wieder für 100% CPU Auslastung bei einen der beiden Prozessorkerne. Z.B. wenn ich ein neues Lesezeichen hinzufügen möchte, dann geht fast nix mehr.
Systemdaten:
Athlon 64 X2 Dual Core 6000+
Asus M2N SLI-Deluxe
4x 1GB OCZ PC6400
Ich habe viel im Netz gesucht, doch man findet zu jeder Fehlermeldung nahezu jede mögliche Fehlerursache als Erklärung, was im Endeffekt leider nicht weiter führt. Irgendwann bin ich dann über das Debugging Tool und die Crash Dumps gestolpert und habe versucht, mich da einzuarbeiten. Leider ist das aber so komplex, dass ich da nicht weiter komme.
Jedenfalls klang es für mich immer wieder so, als würde Information im Arbeitsspeicher verloren gehen, nicht zuletzt wegen dem zuletzt aufgelisteten Fehler 0xD6.
Ich habe dann Memtest laufen lassen. Komischerweise prüft Memtest zunächst 0 - 2048 MB, dann aber 2048 - 3583 MB und anschließend noch 4096 - 4608 MB? Da kann doch was nicht stimmen?
Es werden aber keine Fehler gefunden, auch nach Stunden nicht.
Wenn ich unter configuration den Arbeitsspeicher erkennen lasse, dann zeigt Memtest nur 3838 MB an und hängt sich nach wenigen Sekunden komplett auf.
Ich habe dann jeden Speicher einzeln getestet, keine Fehler, das System läuft auch.
Bestätigt wird das Ganze durch diesen Arbeitsspeichertest von Microsoft auf der Ultimate Boot Disk. Da bekam ich eine Meldung die in etwa so lautete: Ein Teil des Arbeitsspeichers kann nicht überprüft werden, da er außerhalb des gültigen Bereiches liegt (müsste ich nochmal genau nachschauen).
(Erwähnenswert in dem Zusammenhang sei noch, dass unter dem alten Win XP eine Festplatte mit 500GB zuletzt mit 2048GB angezeigt wurde. Eine zweite 500GB Platte wurde teilweise richtig angezeigt, teilweise aber auch mit 2048GB. Beide Platten sind aktuell NICHT verbaut.)
Mein Gedanke ist aktuell, dass vllt das Board einen Fehler hat? Worüber läuft denn die Ansteuerung der RAMs?
Dann habe ich gelesen, dass man über Start -Ausführen - sfc /scannow die Systemdateien überprüfen kann. Das habe ich gemacht, seither sind die Bluescreens etwas seltener geworden (alle 10-15 Startvorgänge), aber das hängende System bleibt.
Als nächstes habe ich mir den Verifier angeschaut. Hier habe ich mal alle möglichen Überprüfungen laufen lassen, werde aber aus den Ergebnissen nicht wirklich schlau.
Jedenfalls kamen mir 3 Dinge komisch vor:
1. Bei "Erfolgreiche Poolzuweisung ohne Kennung" steht 1
2. Wenn ich die Datenträger-Integritätüberprüfung aktiviere, bekomme ich beim Hochfahren immer folgenden Bluescreen: IO system verification error in crcdisk.sys (WDM Driver Error 226) [crcdisk.sys+1a70 at FFFFFADF90CSCA70]
3. Wenn ich die erweiterte E/A Prüfung aktiviere, bekomme ich immer einen der folgenden beiden Bluescreens:
- 0x35 no_more_IRP_stack_locations
- 0x50 page_fault_in_nonpaged_area
Kann mir jemand sagen, was das alles bedeuten könnte?
Schließlich habe ich noch WhoCrashed laufen lassen. Da steht allerdings überall nur, dass es ein Treiberfehler ist. Auch bei dem Debugging Tool von MS erhalte ich immer wieder Hinweise auf Treiber. Jedoch sind es immer wieder andere Treiber. Und es sind ja vermutlich nicht mehrere beschädigt.
Ich hoffe, dass mir hier jemand weiterhelfen kann. So langsam weiß ich nicht mehr, was ich machen soll...
Im folgenden Beitrag noch ein paar Ergebnisse vom Debugging Tool und WhoCrashed, vllt kann jemand was damit anfangen.