Hallo,
ich habe mir im Eigenbau einen PC erstellt, mit Übertaktung der CPU. Das ganze lief jetzt ~1 Jahr fehlerfrei, doch seit ein paar Wochen tauchen sporadisch (alle paar Tage) BSODs auf. Ich tippe auf einen defekten RAM-Riegel. Die CPU ist auf 4.000MHZ übertaktet. Da das System 1 Jahr stabil lief, dachte ich eigentlich, dass mit Spannungen und Timings alles in Ordnung sein müsste. Allerdings lässt mich der Memtest etwas stutzig werden (siehe Bild ganz unten). Als RAM sind 2 Riegel von Corsair verbaut: CMX8GX3M2A1333C9
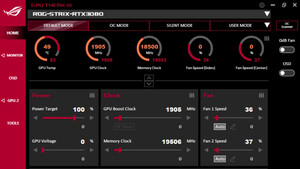
Anbei Screenshots von CPU-Z






Blue-Screen Dump Files mit dem 0x00000050 und 0x0000003B Fehlern:
Memtest-Error:

Ist das normal, dass bei einem fehlerhaften RAM gleich 2598,3MB im Eimer sein können?!?!? Dieser hohe Wert macht mich eben stutzig ob eben nicht doch etwas mit Spannungen und Timings fehlerhaft ist. Kann das MOBO defekt sein?
Vielen Dank für eure Hilfe!
ich habe mir im Eigenbau einen PC erstellt, mit Übertaktung der CPU. Das ganze lief jetzt ~1 Jahr fehlerfrei, doch seit ein paar Wochen tauchen sporadisch (alle paar Tage) BSODs auf. Ich tippe auf einen defekten RAM-Riegel. Die CPU ist auf 4.000MHZ übertaktet. Da das System 1 Jahr stabil lief, dachte ich eigentlich, dass mit Spannungen und Timings alles in Ordnung sein müsste. Allerdings lässt mich der Memtest etwas stutzig werden (siehe Bild ganz unten). Als RAM sind 2 Riegel von Corsair verbaut: CMX8GX3M2A1333C9
Anbei Screenshots von CPU-Z






Blue-Screen Dump Files mit dem 0x00000050 und 0x0000003B Fehlern:
Code:
BugCheck 50, {ffffdb00c2115018, 1, fffff8000300d147, 7}
Could not read faulting driver name
Probably caused by : win32k.sys ( win32k!AllocateObject+dd )
Followup: MachineOwner
---------
6: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
PAGE_FAULT_IN_NONPAGED_AREA (50)
Invalid system memory was referenced. This cannot be protected by try-except,
it must be protected by a Probe. Typically the address is just plain bad or it
is pointing at freed memory.
Arguments:
Arg1: ffffdb00c2115018, memory referenced.
Arg2: 0000000000000001, value 0 = read operation, 1 = write operation.
Arg3: fffff8000300d147, If non-zero, the instruction address which referenced the bad memory
address.
Arg4: 0000000000000007, (reserved)
Debugging Details:
------------------
Could not read faulting driver name
WRITE_ADDRESS: GetPointerFromAddress: unable to read from fffff80003110100
ffffdb00c2115018
FAULTING_IP:
nt!ExAllocatePoolWithTag+537
fffff800`0300d147 48895808 mov qword ptr [rax+8],rbx
MM_INTERNAL_CODE: 7
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x50
PROCESS_NAME: explorer.exe
CURRENT_IRQL: 0
TRAP_FRAME: fffff8800982b3e0 -- (.trap 0xfffff8800982b3e0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=ffffdb00c2115010 rbx=fffff8800982b5c0 rcx=fffff900c2196010
rdx=0000000000000878 rsi=0000000000000001 rdi=0000000000000000
rip=fffff8000300d147 rsp=fffff8800982b570 rbp=0000000000001000
r8=0000000000000021 r9=fffff880042f5680 r10=fffff880042f4cc8
r11=0000000000000008 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl zr na po nc
nt!ExAllocatePoolWithTag+0x537:
fffff800`0300d147 48895808 mov qword ptr [rax+8],rbx ds:0001:ffffdb00`c2115018=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff80002f5552b to fffff80002ed8c00
STACK_TEXT:
fffff880`0982b278 fffff800`02f5552b : 00000000`00000050 ffffdb00`c2115018 00000000`00000001 fffff880`0982b3e0 : nt!KeBugCheckEx
fffff880`0982b280 fffff800`02ed6d2e : 00000000`00000001 ffffdb00`c2115018 fffff900`c1c04900 fffff880`042f5680 : nt! ?? ::FNODOBFM::`string'+0x43781
fffff880`0982b3e0 fffff800`0300d147 : fffff880`0982b760 fffff960`0026c4d3 00000000`00000000 00000001`00000001 : nt!KiPageFault+0x16e
fffff880`0982b570 fffff960`00194c05 : 00000000`00000000 00000000`00000000 00000000`00000000 fffff960`00000000 : nt!ExAllocatePoolWithTag+0x537
fffff880`0982b660 fffff960`001962be : 00000000`00000001 fffff880`0982b7f8 00000000`00000001 fffff960`001a65ce : win32k!AllocateObject+0xdd
fffff880`0982b6a0 fffff960`0016bb67 : fffff880`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : win32k!SURFMEM::bCreateDIB+0x38a
fffff880`0982b790 fffff960`0016d8b1 : 00000000`03010050 00000000`00000014 00000000`00000000 00000000`2e051e32 : win32k!GreCreateDIBitmapReal+0x533
fffff880`0982b8c0 fffff960`0016d6cd : 00000000`0404eae0 fffff900`c21b5630 fffff880`0982bb70 fffff880`0982ba50 : win32k!ProcessAlphaBitmap+0x109
fffff880`0982b9a0 fffff960`0016dd01 : fffff900`c21b5630 00000000`00000000 fffff900`c21b5630 fffff960`002e1c60 : win32k!SetCursorIconData+0x365
fffff880`0982b9f0 fffff800`02ed7e93 : fffffa80`09922590 00000000`00000000 00000000`00000020 ffffffff`90011f1a : win32k!NtUserSetCursorIconData+0x221
fffff880`0982baf0 00000000`7743eafa : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`0404e9f8 fffff800`02ed0250 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x7743eafa
fffff880`0982bcd0 00000000`00000000 : 00000000`00000000 00000000`00000000 fffff960`001a639d 00000000`00000000 : nt!KiCallUserMode
STACK_COMMAND: kb
FOLLOWUP_IP:
win32k!AllocateObject+dd
fffff960`00194c05 488bd8 mov rbx,rax
SYMBOL_STACK_INDEX: 4
SYMBOL_NAME: win32k!AllocateObject+dd
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: win32k
IMAGE_NAME: win32k.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 51aeb1a7
FAILURE_BUCKET_ID: X64_0x50_win32k!AllocateObject+dd
BUCKET_ID: X64_0x50_win32k!AllocateObject+dd
Followup: MachineOwner
Code:
BugCheck 50, {ffffc6a0043d8278, 1, fffff80002ffd147, 7}
Could not read faulting driver name
Probably caused by : msrpc.sys ( msrpc!RpcpDuplicateTokenEx+6b )
Followup: MachineOwner
---------
0: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
PAGE_FAULT_IN_NONPAGED_AREA (50)
Invalid system memory was referenced. This cannot be protected by try-except,
it must be protected by a Probe. Typically the address is just plain bad or it
is pointing at freed memory.
Arguments:
Arg1: ffffc6a0043d8278, memory referenced.
Arg2: 0000000000000001, value 0 = read operation, 1 = write operation.
Arg3: fffff80002ffd147, If non-zero, the instruction address which referenced the bad memory
address.
Arg4: 0000000000000007, (reserved)
Debugging Details:
------------------
Could not read faulting driver name
WRITE_ADDRESS: GetPointerFromAddress: unable to read from fffff80003100100
ffffc6a0043d8278
FAULTING_IP:
nt!ExAllocatePoolWithTag+537
fffff800`02ffd147 48895808 mov qword ptr [rax+8],rbx
MM_INTERNAL_CODE: 7
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x50
PROCESS_NAME: realplay.exe
CURRENT_IRQL: 0
TRAP_FRAME: fffff8800cfc8fe0 -- (.trap 0xfffff8800cfc8fe0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=ffffc6a0043d8270 rbx=0000000000000000 rcx=fffff8a00a9592d0
rdx=0000000000000004 rsi=0000000000000001 rdi=0000000000000000
rip=fffff80002ffd147 rsp=fffff8800cfc9170 rbp=0000000000001000
r8=0000000000000001 r9=fffffa8006c6f7b0 r10=fffffa8006c6f508
r11=0000000000000004 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl zr na po nc
nt!ExAllocatePoolWithTag+0x537:
fffff800`02ffd147 48895808 mov qword ptr [rax+8],rbx ds:ffffc6a0`043d8278=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff80002f4552b to fffff80002ec8c00
STACK_TEXT:
fffff880`0cfc8e78 fffff800`02f4552b : 00000000`00000050 ffffc6a0`043d8278 00000000`00000001 fffff880`0cfc8fe0 : nt!KeBugCheckEx
fffff880`0cfc8e80 fffff800`02ec6d2e : 00000000`00000001 ffffc6a0`043d8278 fffff8a0`1339c000 fffffa80`06c6f7b0 : nt! ?? ::FNODOBFM::`string'+0x43781
fffff880`0cfc8fe0 fffff800`02ffd147 : 00000000`00000000 00000000`0000143c 00000000`00000000 fffff880`0cfc91e0 : nt!KiPageFault+0x16e
fffff880`0cfc9170 fffff800`03194f41 : fffff8a0`00000004 00000000`00000002 fffff8a0`12d90a90 00000000`00000000 : nt!ExAllocatePoolWithTag+0x537
fffff880`0cfc9260 fffff800`0316fede : fffff8a0`03479060 fffff880`0cfc9600 00000000`ffffff00 fffff8a0`12d90a60 : nt!SepAppendAdminAceToTokenAcl+0x121
fffff880`0cfc9320 fffff800`02ec7e93 : fffffa80`06fda1c0 fffff880`0cfc95e8 fffff880`0cfc93d8 fffff8a0`10cd2970 : nt!NtDuplicateToken+0x196
fffff880`0cfc93c0 fffff800`02ec4450 : fffff880`01087c2b 00000000`00000001 fffff880`0108b076 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
fffff880`0cfc95c8 fffff880`01087c2b : 00000000`00000001 fffff880`0108b076 00000000`00000000 fffff8a0`00000000 : nt!KiServiceLinkage
fffff880`0cfc95d0 fffff880`01089d6f : fffffa80`06fda1c0 fffff8a0`02189290 00000000`00000001 cd637052`0022efb4 : msrpc!RpcpDuplicateTokenEx+0x6b
fffff880`0cfc9650 fffff880`0108ae6b : fffff8a0`10cd2970 fffff880`0cfa1b60 fffff8a0`10cd2970 fffff8a0`02189290 : msrpc!LRPC_BASE_BINDING_HANDLE::BaseBindingCopy+0x1bf
fffff880`0cfc9790 fffff880`010881a2 : fffff8a0`02189290 fffff8a0`02189290 00000000`00000050 00000000`00000058 : msrpc!LRPC_FAST_BINDING_HANDLE::BindingCopy+0x8b
fffff880`0cfc97c0 fffff960`0036c4f3 : fffff8a0`0c8782e0 00000000`00000000 00000000`000ae898 00000000`000007ff : msrpc!RpcBindingCopy+0x42
fffff880`0cfc97f0 fffff960`000e3f75 : 00000000`00000000 fffff900`c223bc20 fffff900`c202ace0 00000000`00000000 : win32k!PlaySoundPostMessage+0x77
fffff880`0cfc9850 fffff960`001297a5 : fffffa80`0705f6a0 fffffa80`06fda1c0 fffff880`0cfa1b60 fffff900`c202ace0 : win32k!PostPlaySoundMessage+0x25
fffff880`0cfc9880 fffff960`00132eb9 : 00000000`0000004a 00000000`00000000 00000000`00000000 fffff900`c223bc20 : win32k!PlayEventSound+0x25
fffff880`0cfc98b0 fffff960`0015ec43 : 00000000`73662450 00000000`00000000 00000000`00000000 fffffa80`0705f6a0 : win32k!xxxCreateThreadInfo+0xb99
fffff880`0cfc9a20 fffff960`00135ec0 : fffff900`c223bc20 fffffa80`06fda1c0 fffffa80`06fda1c0 ffffffff`80002ac4 : win32k!UserThreadCallout+0xcf
fffff880`0cfc9a50 fffff800`0316f17d : fffffa80`06fda1c0 fffffa80`0705f6a0 fffff6fc`40067cd8 fffff6fc`40067d08 : win32k!W32pThreadCallout+0x78
fffff880`0cfc9a80 fffff800`02ec04fa : fffffa80`06fda1c0 00000000`00000000 00000000`00000020 00000000`736df2bc : nt!PsConvertToGuiThread+0xe9
fffff880`0cfc9ab0 fffff800`02ec805f : fffffa80`0000023a 00000000`00000000 00000000`0022efb0 00000000`7544665f : nt!KiConvertToGuiThread+0xa
fffff880`0cfc9ae0 00000000`73662e09 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceExit+0x1c4
00000000`000ae898 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x73662e09
STACK_COMMAND: kb
FOLLOWUP_IP:
msrpc!RpcpDuplicateTokenEx+6b
fffff880`01087c2b 85c0 test eax,eax
SYMBOL_STACK_INDEX: 8
SYMBOL_NAME: msrpc!RpcpDuplicateTokenEx+6b
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: msrpc
IMAGE_NAME: msrpc.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4ce79334
FAILURE_BUCKET_ID: X64_0x50_msrpc!RpcpDuplicateTokenEx+6b
BUCKET_ID: X64_0x50_msrpc!RpcpDuplicateTokenEx+6b
Followup: MachineOwner
---------
Code:
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 3B, {c0000005, fffff80002e6db05, fffff880089c1360, 0}
Probably caused by : dxgmms1.sys ( dxgmms1!VIDMM_LINEAR_POOL::AllocateBlock+13c )
Followup: MachineOwner
---------
2: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
SYSTEM_SERVICE_EXCEPTION (3b)
An exception happened while executing a system service routine.
Arguments:
Arg1: 00000000c0000005, Exception code that caused the bugcheck
Arg2: fffff80002e6db05, Address of the exception record for the exception that caused the bugcheck
Arg3: fffff880089c1360, Address of the context record for the exception that caused the bugcheck
Arg4: 0000000000000000, zero.
Debugging Details:
------------------
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - Die Anweisung in 0x%08lx verweist auf Speicher 0x%08lx. Der Vorgang %s konnte nicht im Speicher durchgef hrt werden.
FAULTING_IP:
nt!ExpInterlockedPopEntrySListFault16+0
fffff800`02e6db05 498b08 mov rcx,qword ptr [r8]
CONTEXT: fffff880089c1360 -- (.cxr 0xfffff880089c1360)
rax=000000147ab0006a rbx=fffff8a00fe24d30 rcx=fffff88002f66780
rdx=ffff00a0119e3a21 rsi=0000000000000005 rdi=0000000000000001
rip=fffff80002e6db05 rsp=fffff880089c1d40 rbp=fffff88002f66780
r8=ffff00a0119e3a20 r9=fffff80002e00000 r10=fffff88002f66780
r11=0000000000000000 r12=fffffa8006c6b000 r13=0000000000000000
r14=0000000000000002 r15=000000006d4d6956
iopl=0 nv up ei ng nz na pe nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00010282
nt!ExpInterlockedPopEntrySListFault16:
fffff800`02e6db05 498b08 mov rcx,qword ptr [r8] ds:002b:ffff00a0`119e3a20=????????????????
Resetting default scope
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x3B
PROCESS_NAME: l2.exe.exe
CURRENT_IRQL: 0
LAST_CONTROL_TRANSFER: from fffff80002fa9e80 to fffff80002e6db05
STACK_TEXT:
fffff880`089c1d40 fffff800`02fa9e80 : 00000000`000000a0 00001f80`00000000 00000002`00000048 00000000`00000000 : nt!ExpInterlockedPopEntrySListFault16
fffff880`089c1d50 fffff880`04837e00 : ffffd319`2543bfe2 fffff8a0`0fe24d30 fffff8a0`1186ca50 fffff8a0`1186ca58 : nt!ExAllocatePoolWithTag+0x270
fffff880`089c1e40 fffff880`04837933 : fffff8a0`0fe24d30 00000000`001f0000 00000000`00000000 fffff880`049ae508 : dxgmms1!VIDMM_LINEAR_POOL::AllocateBlock+0x13c
fffff880`089c1e70 fffff880`04837622 : fffff8a0`0fe24d30 00000000`00001000 fffffa80`0a994d90 fffffa80`0a994d90 : dxgmms1!VIDMM_LINEAR_POOL::SplitBlock+0x7b
fffff880`089c1ec0 fffff880`048353d4 : fffffa80`0a5a0b30 fffff8a0`0cbe9010 fffffa80`0784d0f0 fffff8a0`0d5a9120 : dxgmms1!VIDMM_LINEAR_POOL::Allocate+0x2ae
fffff880`089c1f70 fffff880`04834e43 : 00002005`00000000 fffffa80`0a5a0b30 fffff880`00001000 fffff880`05385e1c : dxgmms1!VIDMM_PROCESS_HEAP::AllocateSmallAllocation+0x160
fffff880`089c2030 fffff880`04820a9e : 00000000`00000174 00000000`00001000 fffff8a0`0bbe2ab0 00000000`000007ff : dxgmms1!VIDMM_PROCESS_HEAP::Allocate+0xcf
fffff880`089c20d0 fffff880`0481b01d : fffffa80`089d0000 00000000`00000000 fffffa80`096f8100 fffff8a0`0bbe2ab0 : dxgmms1!VIDMM_GLOBAL::OpenLocalAllocation+0x576
fffff880`089c2170 fffff880`04801aa7 : fffff8a0`1092ec50 fffff8a0`0e981810 fffff880`089c29f0 00000000`00000000 : dxgmms1!VIDMM_GLOBAL::OpenOneAllocation+0x27d
fffff880`089c2260 fffff880`053494bd : 00000000`00000000 fffff880`089c2770 00000000`00000000 fffff8a0`0f7774b0 : dxgmms1!VidMmOpenAllocation+0xeb
fffff880`089c22b0 fffff880`05342a5a : fffff880`089c2558 fffff8a0`0d6ae540 fffff880`089c2730 fffff880`089c2730 : dxgkrnl!DXGDEVICE::CreateVidMmAllocations<_DXGK_ALLOCATIONINFO>+0x291
fffff880`089c2340 fffff880`053455b7 : fffff8a0`0df5b000 fffff880`089c29f0 fffff880`089c2b01 00000000`00000000 : dxgkrnl!DXGDEVICE::CreateAllocation+0x10ae
fffff880`089c2980 fffff960`0027116e : 00000000`0008e2e0 ffffffff`c000aa00 00000000`0008fd20 00000000`000007d3 : dxgkrnl!DxgkCreateAllocation+0x42b
fffff880`089c2ab0 fffff800`02e74e93 : fffffa80`09ee5b50 00000000`0000141c fffff880`089c2ab8 fffffa80`0aed88c0 : win32k!NtGdiDdDDICreateAllocation+0x12
fffff880`089c2ae0 00000000`73f013aa : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`0008e298 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x73f013aa
FOLLOWUP_IP:
dxgmms1!VIDMM_LINEAR_POOL::AllocateBlock+13c
fffff880`04837e00 488bf8 mov rdi,rax
SYMBOL_STACK_INDEX: 2
SYMBOL_NAME: dxgmms1!VIDMM_LINEAR_POOL::AllocateBlock+13c
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: dxgmms1
IMAGE_NAME: dxgmms1.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 5164dc13
STACK_COMMAND: .cxr 0xfffff880089c1360 ; kb
FAILURE_BUCKET_ID: X64_0x3B_dxgmms1!VIDMM_LINEAR_POOL::AllocateBlock+13c
BUCKET_ID: X64_0x3B_dxgmms1!VIDMM_LINEAR_POOL::AllocateBlock+13c
Followup: MachineOwner
---------Memtest-Error:

Ist das normal, dass bei einem fehlerhaften RAM gleich 2598,3MB im Eimer sein können?!?!? Dieser hohe Wert macht mich eben stutzig ob eben nicht doch etwas mit Spannungen und Timings fehlerhaft ist. Kann das MOBO defekt sein?
Vielen Dank für eure Hilfe!