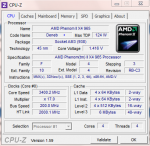
Schranzoid
Ensign
- Registriert
- Juni 2008
- Beiträge
- 140
In letzter Zeit bekomme ich häufig einen Bluescreen, Memtest 86, Chdkisc, Defragmentierung wurde bereits dürchgeführt, ergab aber keine Fehler.
Tritt häufig auf wenn ich z.b. Videos umwandle im normalen Windows Betrieb. Im abgesicherten Modus läuft alles sauber ohne Abstürze.
Anbei das Minidump:
Microsoft (R) Windows Debugger Version 6.11.0001.402 X86
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\082913-34531-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: srv*c:\websymbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 7601.18205.amd64fre.win7sp1_gdr.130708-1532
Machine Name:
Kernel base = 0xfffff800`03c4c000 PsLoadedModuleList = 0xfffff800`03e8f6d0
Debug session time: Thu Aug 29 21:44:50.872 2013 (GMT+2)
System Uptime: 0 days 2:04:36.137
Loading Kernel Symbols
...............................................................
................................................................
.....................................................
Loading User Symbols
Loading unloaded module list
..............
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 1E, {0, 0, 0, 0}
Probably caused by : ntkrnlmp.exe ( nt!KiKernelCalloutExceptionHandler+e )
Followup: MachineOwner
---------
2: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
KMODE_EXCEPTION_NOT_HANDLED (1e)
This is a very common bugcheck. Usually the exception address pinpoints
the driver/function that caused the problem. Always note this address
as well as the link date of the driver/image that contains this address.
Arguments:
Arg1: 0000000000000000, The exception code that was not handled
Arg2: 0000000000000000, The address that the exception occurred at
Arg3: 0000000000000000, Parameter 0 of the exception
Arg4: 0000000000000000, Parameter 1 of the exception
Debugging Details:
------------------
EXCEPTION_CODE: (Win32) 0 (0) - Der Vorgang wurde erfolgreich beendet.
FAULTING_IP:
+6ed9952f04dedb6c
00000000`00000000 ?? ???
EXCEPTION_PARAMETER1: 0000000000000000
EXCEPTION_PARAMETER2: 0000000000000000
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x1E
PROCESS_NAME: System
CURRENT_IRQL: 0
EXCEPTION_RECORD: fffff8800318ca68 -- (.exr 0xfffff8800318ca68)
ExceptionAddress: fffff80003cca341 (nt!PoIdle+0x0000000000000161)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 0000000000000000
Parameter[1]: 0000000003168988
Attempt to read from address 0000000003168988
TRAP_FRAME: fffff8800318cb10 -- (.trap 0xfffff8800318cb10)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=000000063b369af4 rbx=0000000000000000 rcx=000000063b369af4
rdx=0000000000000033 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80003cca341 rsp=fffff8800318cca0 rbp=0000000000000000
r8=0000000600000033 r9=0000000000369e99 r10=000000007d5ad71e
r11=fffffa8009372c10 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up di ng nz na po nc
nt!PoIdle+0x161:
fffff800`03cca341 488b8608480000 mov rax,qword ptr [rsi+4808h] ds:4d08:00000000`00004808=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff80003cb957e to fffff80003cc1b50
STACK_TEXT:
fffff880`0318bb48 fffff800`03cb957e : 00000000`00000000 fffffa80`07886080 fffff880`0318c2c0 fffff800`03ceca90 : nt!KeBugCheck
fffff880`0318bb50 fffff800`03cec75d : fffff800`03ed00bc fffff800`03e0ea80 fffff800`03c4c000 fffff880`0318ca68 : nt!KiKernelCalloutExceptionHandler+0xe
fffff880`0318bb80 fffff800`03ceb535 : fffff800`03e11038 fffff880`0318bbf8 fffff880`0318ca68 fffff800`03c4c000 : nt!RtlpExecuteHandlerForException+0xd
fffff880`0318bbb0 fffff800`03cfc4e1 : fffff880`0318ca68 fffff880`0318c2c0 fffff880`00000000 fffffa80`09383b50 : nt!RtlDispatchException+0x415
fffff880`0318c290 fffff800`03cc1202 : fffff880`0318ca68 fffffa80`088989b8 fffff880`0318cb10 00000000`03164180 : nt!KiDispatchException+0x135
fffff880`0318c930 fffff800`03cbfd7a : 00000000`00000000 00000000`03168988 00000000`00000000 fffffa80`088989b8 : nt!KiExceptionDispatch+0xc2
fffff880`0318cb10 fffff800`03cca341 : 00000000`00369e99 fffffa80`088989b8 fffff880`0316efc0 00000000`00000001 : nt!KiPageFault+0x23a
fffff880`0318cca0 fffff800`03cb985c : fffff880`03164180 fffff880`00000000 00000000`00000000 fffff880`055cc4d0 : nt!PoIdle+0x161
fffff880`0318cd80 00000000`00000000 : fffff880`0318d000 fffff880`03187000 fffff880`0318cd40 00000000`00000000 : nt!KiIdleLoop+0x2c
STACK_COMMAND: kb
FOLLOWUP_IP:
nt!KiKernelCalloutExceptionHandler+e
fffff800`03cb957e 90 nop
SYMBOL_STACK_INDEX: 1
SYMBOL_NAME: nt!KiKernelCalloutExceptionHandler+e
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
DEBUG_FLR_IMAGE_TIMESTAMP: 51db806a
FAILURE_BUCKET_ID: X64_0x1E_nt!KiKernelCalloutExceptionHandler+e
BUCKET_ID: X64_0x1E_nt!KiKernelCalloutExceptionHandler+e
Followup: MachineOwner
---------
Tritt häufig auf wenn ich z.b. Videos umwandle im normalen Windows Betrieb. Im abgesicherten Modus läuft alles sauber ohne Abstürze.
Anbei das Minidump:
Microsoft (R) Windows Debugger Version 6.11.0001.402 X86
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\082913-34531-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: srv*c:\websymbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 7601.18205.amd64fre.win7sp1_gdr.130708-1532
Machine Name:
Kernel base = 0xfffff800`03c4c000 PsLoadedModuleList = 0xfffff800`03e8f6d0
Debug session time: Thu Aug 29 21:44:50.872 2013 (GMT+2)
System Uptime: 0 days 2:04:36.137
Loading Kernel Symbols
...............................................................
................................................................
.....................................................
Loading User Symbols
Loading unloaded module list
..............
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 1E, {0, 0, 0, 0}
Probably caused by : ntkrnlmp.exe ( nt!KiKernelCalloutExceptionHandler+e )
Followup: MachineOwner
---------
2: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
KMODE_EXCEPTION_NOT_HANDLED (1e)
This is a very common bugcheck. Usually the exception address pinpoints
the driver/function that caused the problem. Always note this address
as well as the link date of the driver/image that contains this address.
Arguments:
Arg1: 0000000000000000, The exception code that was not handled
Arg2: 0000000000000000, The address that the exception occurred at
Arg3: 0000000000000000, Parameter 0 of the exception
Arg4: 0000000000000000, Parameter 1 of the exception
Debugging Details:
------------------
EXCEPTION_CODE: (Win32) 0 (0) - Der Vorgang wurde erfolgreich beendet.
FAULTING_IP:
+6ed9952f04dedb6c
00000000`00000000 ?? ???
EXCEPTION_PARAMETER1: 0000000000000000
EXCEPTION_PARAMETER2: 0000000000000000
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x1E
PROCESS_NAME: System
CURRENT_IRQL: 0
EXCEPTION_RECORD: fffff8800318ca68 -- (.exr 0xfffff8800318ca68)
ExceptionAddress: fffff80003cca341 (nt!PoIdle+0x0000000000000161)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 0000000000000000
Parameter[1]: 0000000003168988
Attempt to read from address 0000000003168988
TRAP_FRAME: fffff8800318cb10 -- (.trap 0xfffff8800318cb10)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=000000063b369af4 rbx=0000000000000000 rcx=000000063b369af4
rdx=0000000000000033 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80003cca341 rsp=fffff8800318cca0 rbp=0000000000000000
r8=0000000600000033 r9=0000000000369e99 r10=000000007d5ad71e
r11=fffffa8009372c10 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up di ng nz na po nc
nt!PoIdle+0x161:
fffff800`03cca341 488b8608480000 mov rax,qword ptr [rsi+4808h] ds:4d08:00000000`00004808=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff80003cb957e to fffff80003cc1b50
STACK_TEXT:
fffff880`0318bb48 fffff800`03cb957e : 00000000`00000000 fffffa80`07886080 fffff880`0318c2c0 fffff800`03ceca90 : nt!KeBugCheck
fffff880`0318bb50 fffff800`03cec75d : fffff800`03ed00bc fffff800`03e0ea80 fffff800`03c4c000 fffff880`0318ca68 : nt!KiKernelCalloutExceptionHandler+0xe
fffff880`0318bb80 fffff800`03ceb535 : fffff800`03e11038 fffff880`0318bbf8 fffff880`0318ca68 fffff800`03c4c000 : nt!RtlpExecuteHandlerForException+0xd
fffff880`0318bbb0 fffff800`03cfc4e1 : fffff880`0318ca68 fffff880`0318c2c0 fffff880`00000000 fffffa80`09383b50 : nt!RtlDispatchException+0x415
fffff880`0318c290 fffff800`03cc1202 : fffff880`0318ca68 fffffa80`088989b8 fffff880`0318cb10 00000000`03164180 : nt!KiDispatchException+0x135
fffff880`0318c930 fffff800`03cbfd7a : 00000000`00000000 00000000`03168988 00000000`00000000 fffffa80`088989b8 : nt!KiExceptionDispatch+0xc2
fffff880`0318cb10 fffff800`03cca341 : 00000000`00369e99 fffffa80`088989b8 fffff880`0316efc0 00000000`00000001 : nt!KiPageFault+0x23a
fffff880`0318cca0 fffff800`03cb985c : fffff880`03164180 fffff880`00000000 00000000`00000000 fffff880`055cc4d0 : nt!PoIdle+0x161
fffff880`0318cd80 00000000`00000000 : fffff880`0318d000 fffff880`03187000 fffff880`0318cd40 00000000`00000000 : nt!KiIdleLoop+0x2c
STACK_COMMAND: kb
FOLLOWUP_IP:
nt!KiKernelCalloutExceptionHandler+e
fffff800`03cb957e 90 nop
SYMBOL_STACK_INDEX: 1
SYMBOL_NAME: nt!KiKernelCalloutExceptionHandler+e
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
DEBUG_FLR_IMAGE_TIMESTAMP: 51db806a
FAILURE_BUCKET_ID: X64_0x1E_nt!KiKernelCalloutExceptionHandler+e
BUCKET_ID: X64_0x1E_nt!KiKernelCalloutExceptionHandler+e
Followup: MachineOwner
---------