Moin moin,
ich bin am Verzweifeln mit meinem PC, es gibt immer mal wieder Bluescreens. Mit dem Problem schlage ich mich schon ein paar Monate herum und habe die offensichtlichen Fehlerquellen beseitigt.
Treiber, Bios und Firmware sind aktuell
Memtest86 über Nacht laufen lassen -> keine Fehler
Windows 7 neu installiert
neue Grafikkarte gekauft
sämtliche nicht benötigte Peripherie abgenommen
Ich bin mir nicht sicher welche Infos benötigt werden, falls etwas fehlt bitte melden
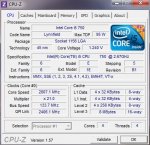
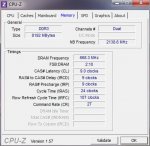
Eine Auswahl meiner Dumpfiles findet sich hier
Anhang anzeigen Dumpfiles.7z
Und hier die Analysierten, letzten beiden Dumpfiles:
Microsoft (R) Windows Debugger Version 6.11.0001.404 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Users\Thomas\Desktop\Dumpfiles\010214-18064-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*C:\symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 7601.18247.amd64fre.win7sp1_gdr.130828-1532
Machine Name:
Kernel base = 0xfffff800`03209000 PsLoadedModuleList = 0xfffff800`0344c6d0
Debug session time: Thu Jan 2 11:05:13.829 2014 (GMT+1)
System Uptime: 0 days 1:22:42.781
Loading Kernel Symbols
...............................................................
................................................................
.......................................
Loading User Symbols
Loading unloaded module list
...........
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 24, {c08a5, 0, 0, 0}
Probably caused by : Ntfs.sys ( Ntfs!NtfsPagingFileIo+155 )
Followup: MachineOwner
---------
0: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
NTFS_FILE_SYSTEM (24)
If you see NtfsExceptionFilter on the stack then the 2nd and 3rd
parameters are the exception record and context record. Do a .cxr
on the 3rd parameter and then kb to obtain a more informative stack
trace.
Arguments:
Arg1: 00000000000c08a5
Arg2: 0000000000000000
Arg3: 0000000000000000
Arg4: 0000000000000000
Debugging Details:
------------------
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x24
PROCESS_NAME: svchost.exe
CURRENT_IRQL: 0
LAST_CONTROL_TRANSFER: from fffff88001a0df15 to fffff8000327ebc0
STACK_TEXT:
fffff880`0b3b66b8 fffff880`01a0df15 : 00000000`00000024 00000000`000c08a5 00000000`00000000 00000000`00000000 : nt!KeBugCheckEx
fffff880`0b3b66c0 fffff880`01a0db68 : 00000001`00000000 00000000`00000000 00000000`00000000 00000800`00000000 : Ntfs!NtfsPagingFileIo+0x155
fffff880`0b3b67c0 fffff880`01602bcf : fffffa80`0d338790 fffffa80`0d3383f0 fffffa80`0dc94010 00000000`00000000 : Ntfs! ?? ::FNODOBFM::`string'+0x7d59
fffff880`0b3b6870 fffff880`016016df : fffffa80`07b28de0 fffffa80`072ad001 fffffa80`07b28d00 fffffa80`0d3383f0 : fltmgr!FltpLegacyProcessingAfterPreCallbacksCompleted+0x24f
fffff880`0b3b6900 fffff800`032a5e15 : fffffa80`0d338410 fffffa80`0afad8b0 fffffa80`0b06bdf0 fffff800`033f9e80 : fltmgr!FltpDispatch+0xcf
fffff880`0b3b6960 fffff800`032a58e9 : 00000000`00000001 00000000`00000001 fffffa80`0b06bd30 fffffa80`0b06bd30 : nt!IoPageRead+0x255
fffff880`0b3b69f0 fffff800`0328c28a : 00000000`00000000 00000000`00000000 ffffffff`ffffffff fffff680`000392a0 : nt!MiIssueHardFault+0x255
fffff880`0b3b6ac0 fffff800`0327ccee : 00000000`00000001 00000000`07255000 00000000`00178d01 00000000`07130c30 : nt!MmAccessFault+0x146a
fffff880`0b3b6c20 00000000`771f67ae : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiPageFault+0x16e
00000000`011be8c0 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x771f67ae
STACK_COMMAND: kb
FOLLOWUP_IP:
Ntfs!NtfsPagingFileIo+155
fffff880`01a0df15 cc int 3
SYMBOL_STACK_INDEX: 1
SYMBOL_NAME: Ntfs!NtfsPagingFileIo+155
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: Ntfs
IMAGE_NAME: Ntfs.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 5167f5fc
FAILURE_BUCKET_ID: X64_0x24_Ntfs!NtfsPagingFileIo+155
BUCKET_ID: X64_0x24_Ntfs!NtfsPagingFileIo+155
Followup: MachineOwner
---------
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
KMODE_EXCEPTION_NOT_HANDLED (1e)
This is a very common bugcheck. Usually the exception address pinpoints
the driver/function that caused the problem. Always note this address
as well as the link date of the driver/image that contains this address.
Arguments:
Arg1: ffffffffc0000005, The exception code that was not handled
Arg2: fffff88007b47960, The address that the exception occurred at
Arg3: 0000000000000000, Parameter 0 of the exception
Arg4: 0000000000000000, Parameter 1 of the exception
Debugging Details:
------------------
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - Die Anweisung in 0x%08lx verweist auf Speicher 0x%08lx. Der Vorgang %s konnte nicht im Speicher durchgef hrt werden.
FAULTING_IP:
+0
fffff880`07b47960 8888b40780f8 mov byte ptr [rax-77FF84Ch],cl
EXCEPTION_PARAMETER1: 0000000000000000
EXCEPTION_PARAMETER2: 0000000000000000
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff80003504100
0000000000000000
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x1E
PROCESS_NAME: System
CURRENT_IRQL: 2
EXCEPTION_RECORD: fffff88007b48888 -- (.exr 0xfffff88007b48888)
ExceptionAddress: fffff88001e4e439 (tcpip!TcpDereferenceTcb+0x0000000000000009)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 0000000000000000
Parameter[1]: ffffffffffffffff
Attempt to read from address ffffffffffffffff
TRAP_FRAME: fffff88007b48930 -- (.trap 0xfffff88007b48930)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=fffffa800b8105b0 rbx=0000000000000000 rcx=7ffffa8006cea260
rdx=fffffa800b87ab71 rsi=0000000000000000 rdi=0000000000000000
rip=fffff88001e4e439 rsp=fffff88007b48ac0 rbp=0000000000000000
r8=fffffa800b87ab70 r9=0000000000000040 r10=fffff880037d5b20
r11=0000000000000002 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei ng nz na po nc
tcpip!TcpDereferenceTcb+0x9:
fffff880`01e4e439 f00fc15908 lock xadd dword ptr [rcx+8],ebx ds:bfe8:7ffffa80`06cea268=????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff8000335e1bb to fffff800032ccbc0
STACK_TEXT:
fffff880`07b48ac0 fffff880`01e4d9a9 : 00000000`000006de 00000000`00000494 00000000`00000000 fffffa80`072a6b30 : tcpip!TcpDereferenceTcb+0x9
fffff880`07b48af0 fffff880`01e62728 : 00000000`00000000 fffff880`07b48d88 00000000`00000000 fffff880`00030000 : tcpip!TcpCompleteTcbSend+0x49
fffff880`07b48b20 fffff880`01e6197a : fffffa80`06cea260 fffff880`01e5a800 fffffa80`07a5d400 fffff880`01e70672 : tcpip!TcpTcbReceive+0x3ec
fffff880`07b48c30 fffff880`01e62aeb : fffffa80`0709e124 00000000`00000000 00000000`00000000 fffff880`07b49000 : tcpip!TcpMatchReceive+0x1fa
fffff880`07b48d80 fffff880`01e5af17 : fffffa80`07bc9490 fffffa80`07a8bb01 fffffa80`00003cc5 00000000`00003cc5 : tcpip!TcpPreValidatedReceive+0x36b
fffff880`07b48e50 fffff880`01e5aa8a : 00000000`00000000 fffff880`01f6d9a0 fffff880`07b49010 fffff880`009eb300 : tcpip!IppDeliverListToProtocol+0x97
fffff880`07b48f10 fffff880`01e5a089 : fffffa80`0a834d28 fffff800`032d5bda 00000000`00000010 fffff880`07b49000 : tcpip!IppProcessDeliverList+0x5a
fffff880`07b48fb0 fffff880`01e57d2f : 00000000`37db1332 fffff880`01f6d9a0 fffff880`01f6d9a0 00000000`00000000 : tcpip!IppReceiveHeaderBatch+0x23a
fffff880`07b49090 fffff880`01e57302 : fffffa80`0bc10800 00000000`00000000 fffffa80`0bd97a01 00000000`00000001 : tcpip!IpFlcReceivePackets+0x64f
fffff880`07b49290 fffff880`01e5672a : fffffa80`0bd97a10 fffff880`07b493c0 fffffa80`0bd97a10 fffffa80`0c3a0000 : tcpip!FlpReceiveNonPreValidatedNetBufferListChain+0x2b2
fffff880`07b49370 fffff800`032d8878 : fffffa80`076411d0 00000000`00004800 fffffa80`0bd69b50 00000000`00000000 : tcpip!FlReceiveNetBufferListChainCalloutRoutine+0xda
fffff880`07b493c0 fffff880`01e56e22 : fffff880`01e56650 fffffa80`0bc2d030 fffffa80`10cc6202 00000000`00000000 : nt!KeExpandKernelStackAndCalloutEx+0xd8
fffff880`07b494a0 fffff880`01d7f0eb : fffffa80`0b9ff010 00000000`00000000 fffffa80`0a7c61a0 fffffa80`0a7c61a0 : tcpip!FlReceiveNetBufferListChain+0xb2
fffff880`07b49510 fffff880`01d48ad6 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : ndis!ndisMIndicateNetBufferListsToOpen+0xdb
fffff880`07b49580 fffff880`01ccb5d4 : fffffa80`0a7c61a0 00000000`00000002 00000000`00000001 fffffa80`076411d0 : ndis!ndisMDispatchReceiveNetBufferLists+0x1d6
fffff880`07b49a00 fffff880`01ccb549 : 00000000`00000000 00000000`00000000 fffffa80`0ba15810 00000000`00000001 : ndis!ndisMTopReceiveNetBufferLists+0x24
fffff880`07b49a40 fffff880`01ccb4e0 : fffff880`079e25c0 fffffa80`0c103010 fffffa80`0ba15810 00000000`00000001 : ndis!ndisFilterIndicateReceiveNetBufferLists+0x29
fffff880`07b49a80 fffff880`079ab7ee : fffffa80`0c103010 00000000`00000000 fffffa80`076411d0 fffff880`079e25c0 : ndis!NdisFIndicateReceiveNetBufferLists+0x50
fffff880`07b49ac0 fffff880`01ccb549 : fffffa80`0bd85c80 00000000`00000000 00000000`00000001 fffff880`06e28750 : nwifi!Pt6Receive+0x296
fffff880`07b49b20 fffff880`01ccb4e0 : fffffa80`0c0fd028 fffff880`04a300c7 fffff880`04a31340 ffff0000`00000000 : ndis!ndisFilterIndicateReceiveNetBufferLists+0x29
fffff880`07b49b60 fffff880`04a2c9c0 : fffff880`04a33110 00000000`00000000 00000000`00000001 fffffa80`0c0fda78 : ndis!NdisFIndicateReceiveNetBufferLists+0x50
fffff880`07b49ba0 fffff880`01ce40a7 : fffffa80`0a7c61a0 fffffa80`0c773700 fffffa80`0c773700 00000000`00000001 : vwififlt!FilterReceiveNetBufferLists+0x158
fffff880`07b49c00 fffff880`06e45476 : fffffa80`0bd69b50 00000000`00000080 fffffa80`0b62ee28 fffffa80`0bc2d030 : ndis! ?? ::FNODOBFM::`string'+0xcd8f
fffff880`07b49c50 fffffa80`0bd69b50 : 00000000`00000080 fffffa80`0b62ee28 fffffa80`0bc2d030 ffff0000`00000000 : athurx+0x24476
fffff880`07b49c58 00000000`00000080 : fffffa80`0b62ee28 fffffa80`0bc2d030 ffff0000`00000000 fffff880`06e277f3 : 0xfffffa80`0bd69b50
fffff880`07b49c60 fffffa80`0b62ee28 : fffffa80`0bc2d030 ffff0000`00000000 fffff880`06e277f3 00000000`00000000 : 0x80
fffff880`07b49c68 fffffa80`0bc2d030 : ffff0000`00000000 fffff880`06e277f3 00000000`00000000 00000000`00000000 : 0xfffffa80`0b62ee28
fffff880`07b49c70 ffff0000`00000000 : fffff880`06e277f3 00000000`00000000 00000000`00000000 fffffa80`0c773700 : 0xfffffa80`0bc2d030
fffff880`07b49c78 fffff880`06e277f3 : 00000000`00000000 00000000`00000000 fffffa80`0c773700 00000001`00000001 : 0xffff0000`00000000
fffff880`07b49c80 00000000`00000000 : 00000000`00000000 fffffa80`0c773700 00000001`00000001 fffffa80`0bc2d030 : athurx+0x67f3
STACK_COMMAND: .trap 0xfffff88007b48930 ; kb
FOLLOWUP_IP:
nwifi!Pt6Receive+296
fffff880`079ab7ee 83a3e010000000 and dword ptr [rbx+10E0h],0
SYMBOL_STACK_INDEX: 12
SYMBOL_NAME: nwifi!Pt6Receive+296
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nwifi
IMAGE_NAME: nwifi.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4a5bcc3b
FAILURE_BUCKET_ID: X64_0x1E_nwifi!Pt6Receive+296
BUCKET_ID: X64_0x1E_nwifi!Pt6Receive+296
Followup: MachineOwner
---------
Leider gibt es noch diverse anderen Fehlermeldungen, so dass ich total im Dunkel tappe. Kann mir jemand weiterhelfen?
Vielen Dank schon mal
ich bin am Verzweifeln mit meinem PC, es gibt immer mal wieder Bluescreens. Mit dem Problem schlage ich mich schon ein paar Monate herum und habe die offensichtlichen Fehlerquellen beseitigt.
Treiber, Bios und Firmware sind aktuell
Memtest86 über Nacht laufen lassen -> keine Fehler
Windows 7 neu installiert
neue Grafikkarte gekauft
sämtliche nicht benötigte Peripherie abgenommen
Ich bin mir nicht sicher welche Infos benötigt werden, falls etwas fehlt bitte melden



Eine Auswahl meiner Dumpfiles findet sich hier
Anhang anzeigen Dumpfiles.7z
Und hier die Analysierten, letzten beiden Dumpfiles:
Microsoft (R) Windows Debugger Version 6.11.0001.404 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Users\Thomas\Desktop\Dumpfiles\010214-18064-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*C:\symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 7601.18247.amd64fre.win7sp1_gdr.130828-1532
Machine Name:
Kernel base = 0xfffff800`03209000 PsLoadedModuleList = 0xfffff800`0344c6d0
Debug session time: Thu Jan 2 11:05:13.829 2014 (GMT+1)
System Uptime: 0 days 1:22:42.781
Loading Kernel Symbols
...............................................................
................................................................
.......................................
Loading User Symbols
Loading unloaded module list
...........
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 24, {c08a5, 0, 0, 0}
Probably caused by : Ntfs.sys ( Ntfs!NtfsPagingFileIo+155 )
Followup: MachineOwner
---------
0: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
NTFS_FILE_SYSTEM (24)
If you see NtfsExceptionFilter on the stack then the 2nd and 3rd
parameters are the exception record and context record. Do a .cxr
on the 3rd parameter and then kb to obtain a more informative stack
trace.
Arguments:
Arg1: 00000000000c08a5
Arg2: 0000000000000000
Arg3: 0000000000000000
Arg4: 0000000000000000
Debugging Details:
------------------
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x24
PROCESS_NAME: svchost.exe
CURRENT_IRQL: 0
LAST_CONTROL_TRANSFER: from fffff88001a0df15 to fffff8000327ebc0
STACK_TEXT:
fffff880`0b3b66b8 fffff880`01a0df15 : 00000000`00000024 00000000`000c08a5 00000000`00000000 00000000`00000000 : nt!KeBugCheckEx
fffff880`0b3b66c0 fffff880`01a0db68 : 00000001`00000000 00000000`00000000 00000000`00000000 00000800`00000000 : Ntfs!NtfsPagingFileIo+0x155
fffff880`0b3b67c0 fffff880`01602bcf : fffffa80`0d338790 fffffa80`0d3383f0 fffffa80`0dc94010 00000000`00000000 : Ntfs! ?? ::FNODOBFM::`string'+0x7d59
fffff880`0b3b6870 fffff880`016016df : fffffa80`07b28de0 fffffa80`072ad001 fffffa80`07b28d00 fffffa80`0d3383f0 : fltmgr!FltpLegacyProcessingAfterPreCallbacksCompleted+0x24f
fffff880`0b3b6900 fffff800`032a5e15 : fffffa80`0d338410 fffffa80`0afad8b0 fffffa80`0b06bdf0 fffff800`033f9e80 : fltmgr!FltpDispatch+0xcf
fffff880`0b3b6960 fffff800`032a58e9 : 00000000`00000001 00000000`00000001 fffffa80`0b06bd30 fffffa80`0b06bd30 : nt!IoPageRead+0x255
fffff880`0b3b69f0 fffff800`0328c28a : 00000000`00000000 00000000`00000000 ffffffff`ffffffff fffff680`000392a0 : nt!MiIssueHardFault+0x255
fffff880`0b3b6ac0 fffff800`0327ccee : 00000000`00000001 00000000`07255000 00000000`00178d01 00000000`07130c30 : nt!MmAccessFault+0x146a
fffff880`0b3b6c20 00000000`771f67ae : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiPageFault+0x16e
00000000`011be8c0 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x771f67ae
STACK_COMMAND: kb
FOLLOWUP_IP:
Ntfs!NtfsPagingFileIo+155
fffff880`01a0df15 cc int 3
SYMBOL_STACK_INDEX: 1
SYMBOL_NAME: Ntfs!NtfsPagingFileIo+155
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: Ntfs
IMAGE_NAME: Ntfs.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 5167f5fc
FAILURE_BUCKET_ID: X64_0x24_Ntfs!NtfsPagingFileIo+155
BUCKET_ID: X64_0x24_Ntfs!NtfsPagingFileIo+155
Followup: MachineOwner
---------
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
KMODE_EXCEPTION_NOT_HANDLED (1e)
This is a very common bugcheck. Usually the exception address pinpoints
the driver/function that caused the problem. Always note this address
as well as the link date of the driver/image that contains this address.
Arguments:
Arg1: ffffffffc0000005, The exception code that was not handled
Arg2: fffff88007b47960, The address that the exception occurred at
Arg3: 0000000000000000, Parameter 0 of the exception
Arg4: 0000000000000000, Parameter 1 of the exception
Debugging Details:
------------------
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - Die Anweisung in 0x%08lx verweist auf Speicher 0x%08lx. Der Vorgang %s konnte nicht im Speicher durchgef hrt werden.
FAULTING_IP:
+0
fffff880`07b47960 8888b40780f8 mov byte ptr [rax-77FF84Ch],cl
EXCEPTION_PARAMETER1: 0000000000000000
EXCEPTION_PARAMETER2: 0000000000000000
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff80003504100
0000000000000000
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x1E
PROCESS_NAME: System
CURRENT_IRQL: 2
EXCEPTION_RECORD: fffff88007b48888 -- (.exr 0xfffff88007b48888)
ExceptionAddress: fffff88001e4e439 (tcpip!TcpDereferenceTcb+0x0000000000000009)
ExceptionCode: c0000005 (Access violation)
ExceptionFlags: 00000000
NumberParameters: 2
Parameter[0]: 0000000000000000
Parameter[1]: ffffffffffffffff
Attempt to read from address ffffffffffffffff
TRAP_FRAME: fffff88007b48930 -- (.trap 0xfffff88007b48930)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=fffffa800b8105b0 rbx=0000000000000000 rcx=7ffffa8006cea260
rdx=fffffa800b87ab71 rsi=0000000000000000 rdi=0000000000000000
rip=fffff88001e4e439 rsp=fffff88007b48ac0 rbp=0000000000000000
r8=fffffa800b87ab70 r9=0000000000000040 r10=fffff880037d5b20
r11=0000000000000002 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei ng nz na po nc
tcpip!TcpDereferenceTcb+0x9:
fffff880`01e4e439 f00fc15908 lock xadd dword ptr [rcx+8],ebx ds:bfe8:7ffffa80`06cea268=????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff8000335e1bb to fffff800032ccbc0
STACK_TEXT:
fffff880`07b48ac0 fffff880`01e4d9a9 : 00000000`000006de 00000000`00000494 00000000`00000000 fffffa80`072a6b30 : tcpip!TcpDereferenceTcb+0x9
fffff880`07b48af0 fffff880`01e62728 : 00000000`00000000 fffff880`07b48d88 00000000`00000000 fffff880`00030000 : tcpip!TcpCompleteTcbSend+0x49
fffff880`07b48b20 fffff880`01e6197a : fffffa80`06cea260 fffff880`01e5a800 fffffa80`07a5d400 fffff880`01e70672 : tcpip!TcpTcbReceive+0x3ec
fffff880`07b48c30 fffff880`01e62aeb : fffffa80`0709e124 00000000`00000000 00000000`00000000 fffff880`07b49000 : tcpip!TcpMatchReceive+0x1fa
fffff880`07b48d80 fffff880`01e5af17 : fffffa80`07bc9490 fffffa80`07a8bb01 fffffa80`00003cc5 00000000`00003cc5 : tcpip!TcpPreValidatedReceive+0x36b
fffff880`07b48e50 fffff880`01e5aa8a : 00000000`00000000 fffff880`01f6d9a0 fffff880`07b49010 fffff880`009eb300 : tcpip!IppDeliverListToProtocol+0x97
fffff880`07b48f10 fffff880`01e5a089 : fffffa80`0a834d28 fffff800`032d5bda 00000000`00000010 fffff880`07b49000 : tcpip!IppProcessDeliverList+0x5a
fffff880`07b48fb0 fffff880`01e57d2f : 00000000`37db1332 fffff880`01f6d9a0 fffff880`01f6d9a0 00000000`00000000 : tcpip!IppReceiveHeaderBatch+0x23a
fffff880`07b49090 fffff880`01e57302 : fffffa80`0bc10800 00000000`00000000 fffffa80`0bd97a01 00000000`00000001 : tcpip!IpFlcReceivePackets+0x64f
fffff880`07b49290 fffff880`01e5672a : fffffa80`0bd97a10 fffff880`07b493c0 fffffa80`0bd97a10 fffffa80`0c3a0000 : tcpip!FlpReceiveNonPreValidatedNetBufferListChain+0x2b2
fffff880`07b49370 fffff800`032d8878 : fffffa80`076411d0 00000000`00004800 fffffa80`0bd69b50 00000000`00000000 : tcpip!FlReceiveNetBufferListChainCalloutRoutine+0xda
fffff880`07b493c0 fffff880`01e56e22 : fffff880`01e56650 fffffa80`0bc2d030 fffffa80`10cc6202 00000000`00000000 : nt!KeExpandKernelStackAndCalloutEx+0xd8
fffff880`07b494a0 fffff880`01d7f0eb : fffffa80`0b9ff010 00000000`00000000 fffffa80`0a7c61a0 fffffa80`0a7c61a0 : tcpip!FlReceiveNetBufferListChain+0xb2
fffff880`07b49510 fffff880`01d48ad6 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : ndis!ndisMIndicateNetBufferListsToOpen+0xdb
fffff880`07b49580 fffff880`01ccb5d4 : fffffa80`0a7c61a0 00000000`00000002 00000000`00000001 fffffa80`076411d0 : ndis!ndisMDispatchReceiveNetBufferLists+0x1d6
fffff880`07b49a00 fffff880`01ccb549 : 00000000`00000000 00000000`00000000 fffffa80`0ba15810 00000000`00000001 : ndis!ndisMTopReceiveNetBufferLists+0x24
fffff880`07b49a40 fffff880`01ccb4e0 : fffff880`079e25c0 fffffa80`0c103010 fffffa80`0ba15810 00000000`00000001 : ndis!ndisFilterIndicateReceiveNetBufferLists+0x29
fffff880`07b49a80 fffff880`079ab7ee : fffffa80`0c103010 00000000`00000000 fffffa80`076411d0 fffff880`079e25c0 : ndis!NdisFIndicateReceiveNetBufferLists+0x50
fffff880`07b49ac0 fffff880`01ccb549 : fffffa80`0bd85c80 00000000`00000000 00000000`00000001 fffff880`06e28750 : nwifi!Pt6Receive+0x296
fffff880`07b49b20 fffff880`01ccb4e0 : fffffa80`0c0fd028 fffff880`04a300c7 fffff880`04a31340 ffff0000`00000000 : ndis!ndisFilterIndicateReceiveNetBufferLists+0x29
fffff880`07b49b60 fffff880`04a2c9c0 : fffff880`04a33110 00000000`00000000 00000000`00000001 fffffa80`0c0fda78 : ndis!NdisFIndicateReceiveNetBufferLists+0x50
fffff880`07b49ba0 fffff880`01ce40a7 : fffffa80`0a7c61a0 fffffa80`0c773700 fffffa80`0c773700 00000000`00000001 : vwififlt!FilterReceiveNetBufferLists+0x158
fffff880`07b49c00 fffff880`06e45476 : fffffa80`0bd69b50 00000000`00000080 fffffa80`0b62ee28 fffffa80`0bc2d030 : ndis! ?? ::FNODOBFM::`string'+0xcd8f
fffff880`07b49c50 fffffa80`0bd69b50 : 00000000`00000080 fffffa80`0b62ee28 fffffa80`0bc2d030 ffff0000`00000000 : athurx+0x24476
fffff880`07b49c58 00000000`00000080 : fffffa80`0b62ee28 fffffa80`0bc2d030 ffff0000`00000000 fffff880`06e277f3 : 0xfffffa80`0bd69b50
fffff880`07b49c60 fffffa80`0b62ee28 : fffffa80`0bc2d030 ffff0000`00000000 fffff880`06e277f3 00000000`00000000 : 0x80
fffff880`07b49c68 fffffa80`0bc2d030 : ffff0000`00000000 fffff880`06e277f3 00000000`00000000 00000000`00000000 : 0xfffffa80`0b62ee28
fffff880`07b49c70 ffff0000`00000000 : fffff880`06e277f3 00000000`00000000 00000000`00000000 fffffa80`0c773700 : 0xfffffa80`0bc2d030
fffff880`07b49c78 fffff880`06e277f3 : 00000000`00000000 00000000`00000000 fffffa80`0c773700 00000001`00000001 : 0xffff0000`00000000
fffff880`07b49c80 00000000`00000000 : 00000000`00000000 fffffa80`0c773700 00000001`00000001 fffffa80`0bc2d030 : athurx+0x67f3
STACK_COMMAND: .trap 0xfffff88007b48930 ; kb
FOLLOWUP_IP:
nwifi!Pt6Receive+296
fffff880`079ab7ee 83a3e010000000 and dword ptr [rbx+10E0h],0
SYMBOL_STACK_INDEX: 12
SYMBOL_NAME: nwifi!Pt6Receive+296
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nwifi
IMAGE_NAME: nwifi.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4a5bcc3b
FAILURE_BUCKET_ID: X64_0x1E_nwifi!Pt6Receive+296
BUCKET_ID: X64_0x1E_nwifi!Pt6Receive+296
Followup: MachineOwner
---------
Leider gibt es noch diverse anderen Fehlermeldungen, so dass ich total im Dunkel tappe. Kann mir jemand weiterhelfen?
Vielen Dank schon mal



