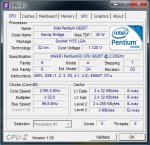
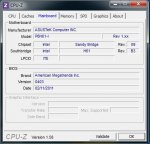
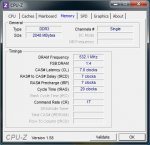
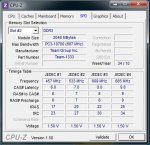
Ich habe mir einen kleinen HTPC zusammengestellt und habe diverse Probleme angefangen damit das die Maus und die Tastatur einfach von jetzt auf gleich aus gehen und enden mit Bluescreens.
Ich Poste mal die Auswertungen der Crashdump in Spoilern vielleicht kann mir jemand helfen :
1
2
3
Ich bitte um Entschuldigung falls ich mit meiner Frage vielleicht der 1000 bin.
Grüße Liturgis
Ich Poste mal die Auswertungen der Crashdump in Spoilern vielleicht kann mir jemand helfen :
1
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\070311-9640-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*C:\symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (2 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 7601.17592.amd64fre.win7sp1_gdr.110408-1631
Machine Name:
Kernel base = 0xfffff800`02a4c000 PsLoadedModuleList = 0xfffff800`02c91650
Debug session time: Sun Jul 3 22:29:52.277 2011 (UTC + 2:00)
System Uptime: 0 days 1:03:02.589
Loading Kernel Symbols
...............................................................
................................................................
...............
Loading User Symbols
Loading unloaded module list
....................
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck D1, {fffff8804b3391b8, 5, 0, fffff8800103c002}
Unable to load image \SystemRoot\system32\DRIVERS\intelppm.sys, Win32 error 0n2
*** WARNING: Unable to verify timestamp for intelppm.sys
*** ERROR: Module load completed but symbols could not be loaded for intelppm.sys
Probably caused by : msahci.sys ( msahci!AhciHwInterrupt+466 )
Followup: MachineOwner
---------
0: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
DRIVER_IRQL_NOT_LESS_OR_EQUAL (d1)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If kernel debugger is available get stack backtrace.
Arguments:
Arg1: fffff8804b3391b8, memory referenced
Arg2: 0000000000000005, IRQL
Arg3: 0000000000000000, value 0 = read operation, 1 = write operation
Arg4: fffff8800103c002, address which referenced memory
Debugging Details:
------------------
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff80002cfb100
fffff8804b3391b8
CURRENT_IRQL: 5
FAULTING_IP:
msahci!AhciHwInterrupt+466
fffff880`0103c002 0f83b1000000 jae msahci!AhciHwInterrupt+0x51d (fffff880`0103c0b9)
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0xD1
PROCESS_NAME: System
TRAP_FRAME: fffff8000405f880 -- (.trap 0xfffff8000405f880)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000000 rbx=0000000000000000 rcx=fffff880033391b8
rdx=0000000080000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff8800103c002 rsp=fffff8000405fa10 rbp=fffffa8003afc6a8
r8=0000000000000029 r9=0000000000000000 r10=fffffa8003afc610
r11=0000000000000000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl zr na po cy
msahci!AhciHwInterrupt+0x466:
fffff880`0103c002 0f83b1000000 jae msahci!AhciHwInterrupt+0x51d (fffff880`0103c0b9) [br=0]
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff80002acb2a9 to fffff80002acbd00
STACK_TEXT:
fffff800`0405f738 fffff800`02acb2a9 : 00000000`0000000a fffff880`4b3391b8 00000000`00000005 00000000`00000000 : nt!KeBugCheckEx
fffff800`0405f740 fffff800`02ac9f20 : fffffa80`05a08502 fffff880`011bf1db 00000000`00000000 00000000`00000000 : nt!KiBugCheckDispatch+0x69
fffff800`0405f880 fffff880`0103c002 : 00000000`00000000 00000000`00000008 00000000`00000008 00000000`00000000 : nt!KiPageFault+0x260
fffff800`0405fa10 fffff800`02ac7939 : fffffa80`00000000 fffffa80`03b0be48 fffff800`0405fb40 fffff800`02a0d895 : msahci!AhciHwInterrupt+0x466
fffff800`0405fa70 fffff800`02ac7718 : 00000000`00000002 fffffa80`043835d0 fffffa80`04fdccf0 fffffa80`00000000 : nt!KiScanInterruptObjectList+0x69
fffff800`0405fac0 fffff880`03c6a9c2 : fffff800`02ad5509 00000000`0020b587 fffffa80`04c10308 fffff800`02c4ccc0 : nt!KiChainedDispatch+0x128
fffff800`0405fc58 fffff800`02ad5509 : 00000000`0020b587 fffffa80`04c10308 fffff800`02c4ccc0 00000000`00000001 : intelppm+0x39c2
fffff800`0405fc60 fffff800`02ac39fc : fffff800`02c3ee80 fffff800`00000000 00000000`00000000 fffff880`02d15588 : nt!PoIdle+0x52a
fffff800`0405fd40 00000000`00000000 : fffff800`04060000 fffff800`0405a000 fffff800`0405fd00 00000000`00000000 : nt!KiIdleLoop+0x2c
STACK_COMMAND: kb
FOLLOWUP_IP:
msahci!AhciHwInterrupt+466
fffff880`0103c002 0f83b1000000 jae msahci!AhciHwInterrupt+0x51d (fffff880`0103c0b9)
SYMBOL_STACK_INDEX: 3
SYMBOL_NAME: msahci!AhciHwInterrupt+466
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: msahci
IMAGE_NAME: msahci.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4ce7a416
FAILURE_BUCKET_ID: X64_0xD1_msahci!AhciHwInterrupt+466
BUCKET_ID: X64_0xD1_msahci!AhciHwInterrupt+466
Followup: MachineOwner
---------
2
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\070311-8970-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*C:\symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (2 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 7601.17514.amd64fre.win7sp1_rtm.101119-1850
Machine Name:
Kernel base = 0xfffff800`02a13000 PsLoadedModuleList = 0xfffff800`02c58e90
Debug session time: Sun Jul 3 01:52:01.521 2011 (UTC + 2:00)
System Uptime: 0 days 0:24:40.848
Loading Kernel Symbols
...............................................................
................................................................
.................
Loading User Symbols
Loading unloaded module list
...........................
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck A, {fffffa84802dfc68, 2, 1, fffff80002ab3881}
Probably caused by : memory_corruption ( nt!MiUnlinkFreeOrZeroedPage+181 )
Followup: MachineOwner
---------
0: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: fffffa84802dfc68, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000001, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff80002ab3881, address which referenced memory
Debugging Details:
------------------
WRITE_ADDRESS: GetPointerFromAddress: unable to read from fffff80002cc40e8
fffffa84802dfc68
CURRENT_IRQL: 2
FAULTING_IP:
nt!MiUnlinkFreeOrZeroedPage+181
fffff800`02ab3881 48893cc2 mov qword ptr [rdx+rax*8],rdi
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0xA
PROCESS_NAME: svchost.exe
TRAP_FRAME: fffff88005b83760 -- (.trap 0xfffff88005b83760)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=000000009005bf8c rbx=0000000000000000 rcx=0000000000000006
rdx=fffffa8000000008 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80002ab3881 rsp=fffff88005b838f0 rbp=0000000000000002
r8=0000000000000000 r9=0000000000000000 r10=fffffa8003012070
r11=fffff80002c05e80 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz na pe nc
nt!MiUnlinkFreeOrZeroedPage+0x181:
fffff800`02ab3881 48893cc2 mov qword ptr [rdx+rax*8],rdi ds:dbb0:fffffa84`802dfc68=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff80002a92be9 to fffff80002a93640
STACK_TEXT:
fffff880`05b83618 fffff800`02a92be9 : 00000000`0000000a fffffa84`802dfc68 00000000`00000002 00000000`00000001 : nt!KeBugCheckEx
fffff880`05b83620 fffff800`02a91860 : fffff8a0`0af23140 00000000`00000000 fffffa80`00000002 fffffa80`00569460 : nt!KiBugCheckDispatch+0x69
fffff880`05b83760 fffff800`02ab3881 : 00000000`071edbc0 00000000`071edb00 00000000`00000003 00000000`00000001 : nt!KiPageFault+0x260
fffff880`05b838f0 fffff800`02ab80b8 : fffff880`05b839c0 00000000`0001cdc2 fffffa80`00569460 00000000`00000000 : nt!MiUnlinkFreeOrZeroedPage+0x181
fffff880`05b83960 fffff800`02aa1844 : 00000000`00000000 00000000`00000002 00000000`00000000 ffffffff`ffffffff : nt!MiRemoveAnyPage+0x1d8
fffff880`05b83a80 fffff800`02a9176e : 00000000`00000001 00000000`078a3000 00000000`00000001 00000000`078282d8 : nt!MmAccessFault+0x1224
fffff880`05b83be0 00000000`706b414d : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiPageFault+0x16e
00000000`071ed648 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x706b414d
STACK_COMMAND: kb
FOLLOWUP_IP:
nt!MiUnlinkFreeOrZeroedPage+181
fffff800`02ab3881 48893cc2 mov qword ptr [rdx+rax*8],rdi
SYMBOL_STACK_INDEX: 3
SYMBOL_NAME: nt!MiUnlinkFreeOrZeroedPage+181
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
DEBUG_FLR_IMAGE_TIMESTAMP: 4ce7951a
IMAGE_NAME: memory_corruption
FAILURE_BUCKET_ID: X64_0xA_nt!MiUnlinkFreeOrZeroedPage+181
BUCKET_ID: X64_0xA_nt!MiUnlinkFreeOrZeroedPage+181
Followup: MachineOwner
---------
0: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: fffffa84802dfc68, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000001, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff80002ab3881, address which referenced memory
Debugging Details:
------------------
WRITE_ADDRESS: fffffa84802dfc68
CURRENT_IRQL: 2
FAULTING_IP:
nt!MiUnlinkFreeOrZeroedPage+181
fffff800`02ab3881 48893cc2 mov qword ptr [rdx+rax*8],rdi
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0xA
PROCESS_NAME: svchost.exe
TRAP_FRAME: fffff88005b83760 -- (.trap 0xfffff88005b83760)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=000000009005bf8c rbx=0000000000000000 rcx=0000000000000006
rdx=fffffa8000000008 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80002ab3881 rsp=fffff88005b838f0 rbp=0000000000000002
r8=0000000000000000 r9=0000000000000000 r10=fffffa8003012070
r11=fffff80002c05e80 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz na pe nc
nt!MiUnlinkFreeOrZeroedPage+0x181:
fffff800`02ab3881 48893cc2 mov qword ptr [rdx+rax*8],rdi ds:dbb0:fffffa84`802dfc68=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff80002a92be9 to fffff80002a93640
STACK_TEXT:
fffff880`05b83618 fffff800`02a92be9 : 00000000`0000000a fffffa84`802dfc68 00000000`00000002 00000000`00000001 : nt!KeBugCheckEx
fffff880`05b83620 fffff800`02a91860 : fffff8a0`0af23140 00000000`00000000 fffffa80`00000002 fffffa80`00569460 : nt!KiBugCheckDispatch+0x69
fffff880`05b83760 fffff800`02ab3881 : 00000000`071edbc0 00000000`071edb00 00000000`00000003 00000000`00000001 : nt!KiPageFault+0x260
fffff880`05b838f0 fffff800`02ab80b8 : fffff880`05b839c0 00000000`0001cdc2 fffffa80`00569460 00000000`00000000 : nt!MiUnlinkFreeOrZeroedPage+0x181
fffff880`05b83960 fffff800`02aa1844 : 00000000`00000000 00000000`00000002 00000000`00000000 ffffffff`ffffffff : nt!MiRemoveAnyPage+0x1d8
fffff880`05b83a80 fffff800`02a9176e : 00000000`00000001 00000000`078a3000 00000000`00000001 00000000`078282d8 : nt!MmAccessFault+0x1224
fffff880`05b83be0 00000000`706b414d : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiPageFault+0x16e
00000000`071ed648 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x706b414d
STACK_COMMAND: kb
FOLLOWUP_IP:
nt!MiUnlinkFreeOrZeroedPage+181
fffff800`02ab3881 48893cc2 mov qword ptr [rdx+rax*8],rdi
SYMBOL_STACK_INDEX: 3
SYMBOL_NAME: nt!MiUnlinkFreeOrZeroedPage+181
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
DEBUG_FLR_IMAGE_TIMESTAMP: 4ce7951a
IMAGE_NAME: memory_corruption
FAILURE_BUCKET_ID: X64_0xA_nt!MiUnlinkFreeOrZeroedPage+181
BUCKET_ID: X64_0xA_nt!MiUnlinkFreeOrZeroedPage+181
Followup: MachineOwner
---------
3
Microsoft (R) Windows Debugger Version 6.12.0002.633 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\070711-8392-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
DbsSplayTreeRangeMap::Add: ignoring zero-sized range at ?fffff800`00b9c4c0?
Symbol search path is: SRV*C:\symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (2 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 7601.17592.amd64fre.win7sp1_gdr.110408-1631
Machine Name:
Kernel base = 0xfffff800`02a54000 PsLoadedModuleList = 0xfffff800`02c99650
Debug session time: Thu Jul 7 03:54:48.896 2011 (UTC + 2:00)
System Uptime: 0 days 2:32:47.223
Loading Kernel Symbols
...............................................................
................................................................
.................
Loading User Symbols
Loading unloaded module list
......
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 9F, {3, fffffa8004c9f060, fffff80000b9c4d8, fffffa8005ed50f0}
Probably caused by : usbhub.sys
Followup: MachineOwner
---------
0: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
DRIVER_POWER_STATE_FAILURE (9f)
A driver is causing an inconsistent power state.
Arguments:
Arg1: 0000000000000003, A device object has been blocking an Irp for too long a time
Arg2: fffffa8004c9f060, Physical Device Object of the stack
Arg3: fffff80000b9c4d8, Functional Device Object of the stack
Arg4: fffffa8005ed50f0, The blocked IRP
Debugging Details:
------------------
DRVPOWERSTATE_SUBCODE: 3
DRIVER_OBJECT: fffffa80043f9ab0
IMAGE_NAME: usbhub.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4ce7a68e
MODULE_NAME: usbhub
FAULTING_MODULE: fffff880040dc000 usbhub
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x9F
PROCESS_NAME: System
CURRENT_IRQL: 2
STACK_TEXT:
fffff800`00b9c488 fffff800`02b409c2 : 00000000`0000009f 00000000`00000003 fffffa80`04c9f060 fffff800`00b9c4d8 : nt!KeBugCheckEx
fffff800`00b9c490 fffff800`02adf652 : fffff800`00b9c5c0 fffff800`00b9c5c0 00000000`00000001 00000000`00000000 : nt! ?? ::FNODOBFM::`string'+0x34a90
fffff800`00b9c530 fffff800`02adf4f6 : fffff800`02c7bf00 00000000`0008f776 00000000`00000000 00000000`00000000 : nt!KiProcessTimerDpcTable+0x66
fffff800`00b9c5a0 fffff800`02adf3de : 00000015`58174e26 fffff800`00b9cc18 00000000`0008f776 fffff800`02c4a148 : nt!KiProcessExpiredTimerList+0xc6
fffff800`00b9cbf0 fffff800`02adf1c7 : 00000004`9350a7c1 00000004`0008f776 00000004`9350a788 00000000`00000076 : nt!KiTimerExpiration+0x1be
fffff800`00b9cc90 fffff800`02acba2a : fffff800`02c46e80 fffff800`02c54cc0 00000000`00000000 fffff880`03c02db0 : nt!KiRetireDpcList+0x277
fffff800`00b9cd40 00000000`00000000 : fffff800`00b9d000 fffff800`00b97000 fffff800`00b9cd00 00000000`00000000 : nt!KiIdleLoop+0x5a
STACK_COMMAND: kb
FOLLOWUP_NAME: MachineOwner
FAILURE_BUCKET_ID: X64_0x9F_3_IMAGE_usbhub.sys
BUCKET_ID: X64_0x9F_3_IMAGE_usbhub.sys
Followup: MachineOwner
---------
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\070711-8392-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
DbsSplayTreeRangeMap::Add: ignoring zero-sized range at ?fffff800`00b9c4c0?
Symbol search path is: SRV*C:\symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (2 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 7601.17592.amd64fre.win7sp1_gdr.110408-1631
Machine Name:
Kernel base = 0xfffff800`02a54000 PsLoadedModuleList = 0xfffff800`02c99650
Debug session time: Thu Jul 7 03:54:48.896 2011 (UTC + 2:00)
System Uptime: 0 days 2:32:47.223
Loading Kernel Symbols
...............................................................
................................................................
.................
Loading User Symbols
Loading unloaded module list
......
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 9F, {3, fffffa8004c9f060, fffff80000b9c4d8, fffffa8005ed50f0}
Probably caused by : usbhub.sys
Followup: MachineOwner
---------
0: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
DRIVER_POWER_STATE_FAILURE (9f)
A driver is causing an inconsistent power state.
Arguments:
Arg1: 0000000000000003, A device object has been blocking an Irp for too long a time
Arg2: fffffa8004c9f060, Physical Device Object of the stack
Arg3: fffff80000b9c4d8, Functional Device Object of the stack
Arg4: fffffa8005ed50f0, The blocked IRP
Debugging Details:
------------------
DRVPOWERSTATE_SUBCODE: 3
DRIVER_OBJECT: fffffa80043f9ab0
IMAGE_NAME: usbhub.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 4ce7a68e
MODULE_NAME: usbhub
FAULTING_MODULE: fffff880040dc000 usbhub
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VISTA_DRIVER_FAULT
BUGCHECK_STR: 0x9F
PROCESS_NAME: System
CURRENT_IRQL: 2
STACK_TEXT:
fffff800`00b9c488 fffff800`02b409c2 : 00000000`0000009f 00000000`00000003 fffffa80`04c9f060 fffff800`00b9c4d8 : nt!KeBugCheckEx
fffff800`00b9c490 fffff800`02adf652 : fffff800`00b9c5c0 fffff800`00b9c5c0 00000000`00000001 00000000`00000000 : nt! ?? ::FNODOBFM::`string'+0x34a90
fffff800`00b9c530 fffff800`02adf4f6 : fffff800`02c7bf00 00000000`0008f776 00000000`00000000 00000000`00000000 : nt!KiProcessTimerDpcTable+0x66
fffff800`00b9c5a0 fffff800`02adf3de : 00000015`58174e26 fffff800`00b9cc18 00000000`0008f776 fffff800`02c4a148 : nt!KiProcessExpiredTimerList+0xc6
fffff800`00b9cbf0 fffff800`02adf1c7 : 00000004`9350a7c1 00000004`0008f776 00000004`9350a788 00000000`00000076 : nt!KiTimerExpiration+0x1be
fffff800`00b9cc90 fffff800`02acba2a : fffff800`02c46e80 fffff800`02c54cc0 00000000`00000000 fffff880`03c02db0 : nt!KiRetireDpcList+0x277
fffff800`00b9cd40 00000000`00000000 : fffff800`00b9d000 fffff800`00b97000 fffff800`00b9cd00 00000000`00000000 : nt!KiIdleLoop+0x5a
STACK_COMMAND: kb
FOLLOWUP_NAME: MachineOwner
FAILURE_BUCKET_ID: X64_0x9F_3_IMAGE_usbhub.sys
BUCKET_ID: X64_0x9F_3_IMAGE_usbhub.sys
Followup: MachineOwner
---------
Ich bitte um Entschuldigung falls ich mit meiner Frage vielleicht der 1000 bin.
Grüße Liturgis