1. Nenne uns bitte deine aktuelle Hardware:
(Bitte tatsächlich hier auflisten und nicht auf Signatur verweisen, da diese von einigen nicht gesehen wird und Hardware sich ändert)
2. Beschreibe dein Problem. Je genauer und besser du dein Problem beschreibst, desto besser kann dir geholfen werden (zusätzliche Bilder könnten z. B. hilfreich sein):
Ich kämpfe seit langem mit Bluescreens und Freezes.
Ich habe herausgefunden, dass die Freezes und BSODs nur auftreten wenn SMT im Bios aktiviert ist.
Mit SMT regnet es auf der aktuellen BIOS Version BSODs und Freezes im 20 Minuten Takt ohne SMT hatte ich bisher einen innerhalb von 3 Tagen.
Leider merke ich die Leistungseinbußen ohne SMT sehr doll, weshalb ich darüber nachdenke meine CPU oder Motherboard auszutauschen.
BSODs habe ich hier mal einen Kernel dump:
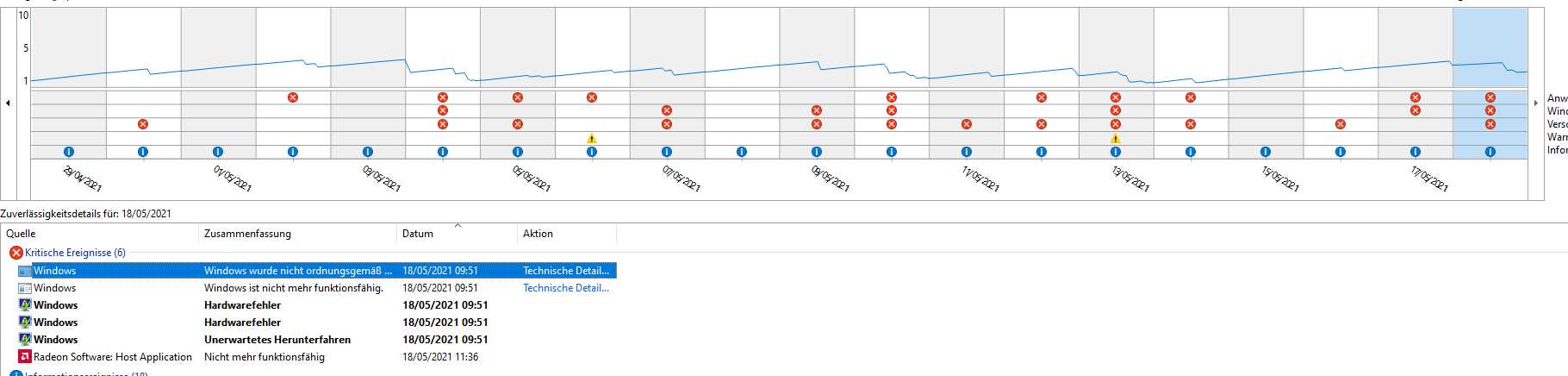
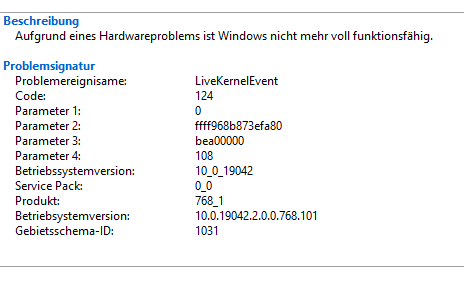
Es sind aber auch diverse andere Bluescreens dabei die meistens immer auf ntkrnlmp.exe oder ähnliche verweisen.
Weitere Bluescreens:
Watchdog Violations,
System Thread Exception
KMODE Exception
Mit Freezes meine ich das das System einfriert und die Bilder noch da bleiben aber ich den PC force resetten muss oder er von alleine ausgeht und neustartet.
3. Welche Schritte hast du bereits unternommen/versucht, um das Problem zu lösen und was hat es gebracht?
-RAM Ausgetauscht
-XMP an/aus
-RAM Voltage bis auf 1,4v hochgeschraubt
-RAM Timings manuell eingegeben
-RAM auf Stock
-RAM mit Memtest einzeln getestet -> Keine Fehler
-Diverse Treiber geupdated
-Alle Bios Versionen ausprobiert:
Auf v30 (ältestes Bios) läuft das System auch mit SMT an so stabil das es nur 2 Mal am Tag abstürzt, auf den neueren Versionen regnet es BSODs und Freezes beim Spielen im 10-20 Minutentakt wenn SMT aktiviert ist.
-Grafikkarte ist nicht gedaisychained
-SSDs verschiedene ausprobiert
-Windows mehrmals neuaufgesetzt
-Grafikkarte undervolted/underclocked
-Prime95, Furmark -> Crashes nicht reproduzierbar
Ich tippe ja auf die CPU oder das Motherboard, wollte aber mal eure Meinung erfragen bevor ich das Geld für eines von beiden raushaue und wieder dumm dastehe. Sehe das gerade als einzige Möglichkeit das Problem irgendwie zu beheben da ich sonst alles ausprobiert habe.
Vielleicht hat einer von euch noch eine Idee?
(Bitte tatsächlich hier auflisten und nicht auf Signatur verweisen, da diese von einigen nicht gesehen wird und Hardware sich ändert)
- Prozessor (CPU): Ryzen 5 3600X
- Arbeitsspeicher (RAM): 2x8GB Corsair RGB Vengeance Pro 3200MhZ
- Mainboard: MSI B450 Tomahawk Max (Aktuellstes Bios)
- Netzteil: Be Quiet 650W 80+ Gold Modular
- Gehäuse: MSI Sekira
- Grafikkarte: Gigabyte RX 5700 XT OC
- HDD / SSD: Crucial 500GB SSD
2. Beschreibe dein Problem. Je genauer und besser du dein Problem beschreibst, desto besser kann dir geholfen werden (zusätzliche Bilder könnten z. B. hilfreich sein):
Ich kämpfe seit langem mit Bluescreens und Freezes.
Ich habe herausgefunden, dass die Freezes und BSODs nur auftreten wenn SMT im Bios aktiviert ist.
Mit SMT regnet es auf der aktuellen BIOS Version BSODs und Freezes im 20 Minuten Takt ohne SMT hatte ich bisher einen innerhalb von 3 Tagen.
Leider merke ich die Leistungseinbußen ohne SMT sehr doll, weshalb ich darüber nachdenke meine CPU oder Motherboard auszutauschen.
BSODs habe ich hier mal einen Kernel dump:
Microsoft (R) Windows Debugger Version 10.0.19041.685 X86
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\MEMORY.DMP]
Kernel Bitmap Dump File: Kernel address space is available, User address space may not be available.
************* Path validation summary **************
Response Time (ms) Location
Deferred Srv*C:\Symbols*http://msdl.microsoft.com/download/symbols
Symbol search path is: Srv*C:\Symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 10 Kernel Version 19041 MP (6 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 19041.1.amd64fre.vb_release.191206-1406
Machine Name:
Kernel base = 0xfffff806`79600000 PsLoadedModuleList = 0xfffff806`7a22a1b0
Debug session time: Tue May 18 09:50:29.593 2021 (UTC + 2:00)
System Uptime: 0 days 0:58:45.231
Loading Kernel Symbols
...............................................................
................................................................
................................................................
..
Loading User Symbols
Loading unloaded module list
..........
For analysis of this file, run !analyze -v
1: kd> !analyze -v
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 00000000006d7d96, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000001, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff8067994992e, address which referenced memory
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.Sec
Value: 3
Key : Analysis.DebugAnalysisProvider.CPP
Value: Create: 8007007e on DESKTOP-MB309I9
Key : Analysis.DebugData
Value: CreateObject
Key : Analysis.DebugModel
Value: CreateObject
Key : Analysis.Elapsed.Sec
Value: 3
Key : Analysis.Memory.CommitPeak.Mb
Value: 73
Key : Analysis.System
Value: CreateObject
BUGCHECK_CODE: a
BUGCHECK_P1: 6d7d96
BUGCHECK_P2: 2
BUGCHECK_P3: 1
BUGCHECK_P4: fffff8067994992e
WRITE_ADDRESS: 00000000006d7d96
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
PROCESS_NAME: System
TRAP_FRAME: fffff60bc9d8d780 -- (.trap 0xfffff60bc9d8d780)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=fffff60bc9d8da78 rbx=0000000000000000 rcx=fffff60bc9d8da78
rdx=00000000006d7d96 rsi=0000000000000000 rdi=0000000000000000
rip=fffff8067994992e rsp=fffff60bc9d8d910 rbp=fffff8067a2dfe50
r8=0000000000000000 r9=ffffaf0e39d09710 r10=fffff8067a2dfe40
r11=0000000000000000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei ng nz na pe nc
nt!KxWaitForLockOwnerShip+0xe:
fffff806`7994992e 48890a mov qword ptr [rdx],rcx ds:00000000`006d7d96=????????????????
Resetting default scope
BAD_STACK_POINTER: fffff60bc9d8d638
STACK_TEXT:
fffff60b`c9d8d638 fffff806`79a08c69 : 00000000`0000000a 00000000`006d7d96 00000000`00000002 00000000`00000001 : nt!KeBugCheckEx
fffff60b`c9d8d640 fffff806`79a04f69 : ffffaf0e`3cf32620 fffff806`799f8d55 fffff60b`c9d8d7b0 fffff60b`c9d8d7a8 : nt!KiBugCheckDispatch+0x69
fffff60b`c9d8d780 fffff806`7994992e : ffffaf0e`3c37da50 fffff60b`c9d8d9b9 ffffaf0e`3c29adb8 fffff806`8adfeaeb : nt!KiPageFault+0x469
fffff60b`c9d8d910 fffff806`79923905 : ffffaf0e`00000000 ffffaf0e`3c37da50 ffffaf0e`38598a60 fffff806`8ad87152 : nt!KxWaitForLockOwnerShip+0xe
fffff60b`c9d8d940 fffff806`79810bf2 : 00000000`00000000 ffffaf0e`35523a60 00000000`00000000 ffffaf0e`35523a60 : nt!KxAcquireQueuedSpinLock+0x55
fffff60b`c9d8d970 fffff806`7980db0d : ffffaf0e`39d09710 fffff60b`c9d8da79 fffff60b`c9d8da78 fffff806`00000000 : nt!KiAbEntryGetLockedHeadEntry+0x262
fffff60b`c9d8da10 fffff806`7988cba3 : ffff9c81`00000000 ffff9c81`00000001 00000009`00000000 00000000`00000000 : nt!KiAbProcessContextSwitch+0x11d
fffff60b`c9d8dae0 fffff806`799fdb36 : fffff806`799f2d00 fffff806`798c656a 00000001`00000001 00000001`00000000 : nt!KiQuantumEnd+0x373
fffff60b`c9d8dbe0 fffff806`799fd3d5 : ffffaf0e`3c0b2760 fffff806`799f8d81 ffffaf0e`3c37da50 fffff60b`c9d8e8d0 : nt!KiDispatchInterruptContinue+0x16
fffff60b`c9d8dc10 fffff806`799f8d81 : ffffaf0e`3c37da50 fffff60b`c9d8e8d0 ffffc180`092698b0 fffff60b`c9d8e120 : nt!KiDpcInterruptBypass+0x25
fffff60b`c9d8dc20 fffff806`8ad819c4 : fffff60b`c9d8e0c0 00000000`00000000 00000000`00000002 00000000`00000001 : nt!KiInterruptDispatchNoLockNoEtw+0xb1
fffff60b`c9d8ddb0 fffff806`89358cc9 : ffffaf0e`39d090c0 ffffc18f`f6439180 ffffaf0e`39d097d0 fffff806`79872e19 : dxgmms2!VidMmReferenceWrittenPrimaries+0x4
fffff60b`c9d8de00 fffff806`893594a1 : ffffc18f`f6a79aa0 00000000`00000001 00000000`00000001 ffffc18f`f6a79aa0 : dxgkrnl!DXGCONTEXT::SubmitCommand+0x3d9
fffff60b`c9d8e5c0 fffff806`893588ad : 00000000`00000020 fffff806`89359f84 ffffc180`00f26cc0 00000027`1961c2d0 : dxgkrnl!DxgkSubmitCommandInternal+0x551
fffff60b`c9d8eac0 fffff806`79a086b8 : ffffaf0e`39d090c0 00000000`00000000 ffffaf0e`3a2e0000 00000001`40000000 : dxgkrnl!DxgkSubmitCommand+0x5d
fffff60b`c9d8eb00 00007ffd`57215ae4 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x28
00000027`1961c208 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ffd`57215ae4
SYMBOL_NAME: nt!KxWaitForLockOwnerShip+e
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: e
FAILURE_BUCKET_ID: AV_STACKPTR_ERROR_nt!KxWaitForLockOwnerShip
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {56c5e1ad-426c-3e07-1dfd-b329bf712cb6}
Followup: MachineOwner
---------
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\MEMORY.DMP]
Kernel Bitmap Dump File: Kernel address space is available, User address space may not be available.
************* Path validation summary **************
Response Time (ms) Location
Deferred Srv*C:\Symbols*http://msdl.microsoft.com/download/symbols
Symbol search path is: Srv*C:\Symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 10 Kernel Version 19041 MP (6 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 19041.1.amd64fre.vb_release.191206-1406
Machine Name:
Kernel base = 0xfffff806`79600000 PsLoadedModuleList = 0xfffff806`7a22a1b0
Debug session time: Tue May 18 09:50:29.593 2021 (UTC + 2:00)
System Uptime: 0 days 0:58:45.231
Loading Kernel Symbols
...............................................................
................................................................
................................................................
..
Loading User Symbols
Loading unloaded module list
..........
For analysis of this file, run !analyze -v
1: kd> !analyze -v
*******************************************************************************
- *
- Bugcheck Analysis *
- *
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 00000000006d7d96, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000001, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff8067994992e, address which referenced memory
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.Sec
Value: 3
Key : Analysis.DebugAnalysisProvider.CPP
Value: Create: 8007007e on DESKTOP-MB309I9
Key : Analysis.DebugData
Value: CreateObject
Key : Analysis.DebugModel
Value: CreateObject
Key : Analysis.Elapsed.Sec
Value: 3
Key : Analysis.Memory.CommitPeak.Mb
Value: 73
Key : Analysis.System
Value: CreateObject
BUGCHECK_CODE: a
BUGCHECK_P1: 6d7d96
BUGCHECK_P2: 2
BUGCHECK_P3: 1
BUGCHECK_P4: fffff8067994992e
WRITE_ADDRESS: 00000000006d7d96
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
PROCESS_NAME: System
TRAP_FRAME: fffff60bc9d8d780 -- (.trap 0xfffff60bc9d8d780)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=fffff60bc9d8da78 rbx=0000000000000000 rcx=fffff60bc9d8da78
rdx=00000000006d7d96 rsi=0000000000000000 rdi=0000000000000000
rip=fffff8067994992e rsp=fffff60bc9d8d910 rbp=fffff8067a2dfe50
r8=0000000000000000 r9=ffffaf0e39d09710 r10=fffff8067a2dfe40
r11=0000000000000000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei ng nz na pe nc
nt!KxWaitForLockOwnerShip+0xe:
fffff806`7994992e 48890a mov qword ptr [rdx],rcx ds:00000000`006d7d96=????????????????
Resetting default scope
BAD_STACK_POINTER: fffff60bc9d8d638
STACK_TEXT:
fffff60b`c9d8d638 fffff806`79a08c69 : 00000000`0000000a 00000000`006d7d96 00000000`00000002 00000000`00000001 : nt!KeBugCheckEx
fffff60b`c9d8d640 fffff806`79a04f69 : ffffaf0e`3cf32620 fffff806`799f8d55 fffff60b`c9d8d7b0 fffff60b`c9d8d7a8 : nt!KiBugCheckDispatch+0x69
fffff60b`c9d8d780 fffff806`7994992e : ffffaf0e`3c37da50 fffff60b`c9d8d9b9 ffffaf0e`3c29adb8 fffff806`8adfeaeb : nt!KiPageFault+0x469
fffff60b`c9d8d910 fffff806`79923905 : ffffaf0e`00000000 ffffaf0e`3c37da50 ffffaf0e`38598a60 fffff806`8ad87152 : nt!KxWaitForLockOwnerShip+0xe
fffff60b`c9d8d940 fffff806`79810bf2 : 00000000`00000000 ffffaf0e`35523a60 00000000`00000000 ffffaf0e`35523a60 : nt!KxAcquireQueuedSpinLock+0x55
fffff60b`c9d8d970 fffff806`7980db0d : ffffaf0e`39d09710 fffff60b`c9d8da79 fffff60b`c9d8da78 fffff806`00000000 : nt!KiAbEntryGetLockedHeadEntry+0x262
fffff60b`c9d8da10 fffff806`7988cba3 : ffff9c81`00000000 ffff9c81`00000001 00000009`00000000 00000000`00000000 : nt!KiAbProcessContextSwitch+0x11d
fffff60b`c9d8dae0 fffff806`799fdb36 : fffff806`799f2d00 fffff806`798c656a 00000001`00000001 00000001`00000000 : nt!KiQuantumEnd+0x373
fffff60b`c9d8dbe0 fffff806`799fd3d5 : ffffaf0e`3c0b2760 fffff806`799f8d81 ffffaf0e`3c37da50 fffff60b`c9d8e8d0 : nt!KiDispatchInterruptContinue+0x16
fffff60b`c9d8dc10 fffff806`799f8d81 : ffffaf0e`3c37da50 fffff60b`c9d8e8d0 ffffc180`092698b0 fffff60b`c9d8e120 : nt!KiDpcInterruptBypass+0x25
fffff60b`c9d8dc20 fffff806`8ad819c4 : fffff60b`c9d8e0c0 00000000`00000000 00000000`00000002 00000000`00000001 : nt!KiInterruptDispatchNoLockNoEtw+0xb1
fffff60b`c9d8ddb0 fffff806`89358cc9 : ffffaf0e`39d090c0 ffffc18f`f6439180 ffffaf0e`39d097d0 fffff806`79872e19 : dxgmms2!VidMmReferenceWrittenPrimaries+0x4
fffff60b`c9d8de00 fffff806`893594a1 : ffffc18f`f6a79aa0 00000000`00000001 00000000`00000001 ffffc18f`f6a79aa0 : dxgkrnl!DXGCONTEXT::SubmitCommand+0x3d9
fffff60b`c9d8e5c0 fffff806`893588ad : 00000000`00000020 fffff806`89359f84 ffffc180`00f26cc0 00000027`1961c2d0 : dxgkrnl!DxgkSubmitCommandInternal+0x551
fffff60b`c9d8eac0 fffff806`79a086b8 : ffffaf0e`39d090c0 00000000`00000000 ffffaf0e`3a2e0000 00000001`40000000 : dxgkrnl!DxgkSubmitCommand+0x5d
fffff60b`c9d8eb00 00007ffd`57215ae4 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x28
00000027`1961c208 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ffd`57215ae4
SYMBOL_NAME: nt!KxWaitForLockOwnerShip+e
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: e
FAILURE_BUCKET_ID: AV_STACKPTR_ERROR_nt!KxWaitForLockOwnerShip
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {56c5e1ad-426c-3e07-1dfd-b329bf712cb6}
Followup: MachineOwner
---------
Es sind aber auch diverse andere Bluescreens dabei die meistens immer auf ntkrnlmp.exe oder ähnliche verweisen.
Weitere Bluescreens:
Watchdog Violations,
System Thread Exception
KMODE Exception
Mit Freezes meine ich das das System einfriert und die Bilder noch da bleiben aber ich den PC force resetten muss oder er von alleine ausgeht und neustartet.
3. Welche Schritte hast du bereits unternommen/versucht, um das Problem zu lösen und was hat es gebracht?
-RAM Ausgetauscht
-XMP an/aus
-RAM Voltage bis auf 1,4v hochgeschraubt
-RAM Timings manuell eingegeben
-RAM auf Stock
-RAM mit Memtest einzeln getestet -> Keine Fehler
-Diverse Treiber geupdated
-Alle Bios Versionen ausprobiert:
Auf v30 (ältestes Bios) läuft das System auch mit SMT an so stabil das es nur 2 Mal am Tag abstürzt, auf den neueren Versionen regnet es BSODs und Freezes beim Spielen im 10-20 Minutentakt wenn SMT aktiviert ist.
-Grafikkarte ist nicht gedaisychained
-SSDs verschiedene ausprobiert
-Windows mehrmals neuaufgesetzt
-Grafikkarte undervolted/underclocked
-Prime95, Furmark -> Crashes nicht reproduzierbar
Ich tippe ja auf die CPU oder das Motherboard, wollte aber mal eure Meinung erfragen bevor ich das Geld für eines von beiden raushaue und wieder dumm dastehe. Sehe das gerade als einzige Möglichkeit das Problem irgendwie zu beheben da ich sonst alles ausprobiert habe.
Vielleicht hat einer von euch noch eine Idee?



