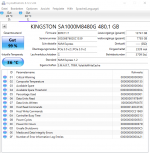
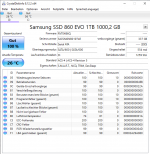
@Silver Server
Okay komisch, bei mir lässt sie sich auswerten.
Microsoft (R) Windows Debugger Version 10.0.21349.1004 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Users\dammy\AppData\Local\Temp\Rar$DIa9468.34433\062321-6046-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
************* Path validation summary **************
Response Time (ms) Location
Deferred srv*
Symbol search path is: srv*
Executable search path is:
Windows 10 Kernel Version 19041 MP (12 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Edition build lab: 19041.1.amd64fre.vb_release.191206-1406
Machine Name:
Kernel base = 0xfffff802`66200000 PsLoadedModuleList = 0xfffff802`66e2a290
Debug session time: Wed Jun 23 21:37:49.197 2021 (UTC + 2:00)
System Uptime: 0 days 14:47:07.846
Loading Kernel Symbols
...............................................................
................................................................
................................................
Loading User Symbols
Loading unloaded module list
...............
For analysis of this file, run !analyze -v
nt!KeBugCheckEx:
fffff802`665f6b90 48894c2408 mov qword ptr [rsp+8],rcx ss:0018:fffffc06`3d4e53c0=000000000000003b
10: kd> !analyze -v
*******************************************************************************
*******************************************************************************
SYSTEM_SERVICE_EXCEPTION (3b)
An exception happened while executing a system service routine.
Arguments:
Arg1: 00000000c0000005, Exception code that caused the BugCheck
Arg2: fffff80266412849, Address of the instruction which caused the BugCheck
Arg3: fffffc063d4e5cc0, Address of the context record for the exception that caused the BugCheck
Arg4: 0000000000000000, zero.
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 3405
Key : Analysis.DebugAnalysisManager
Value: Create
Key : Analysis.Elapsed.mSec
Value: 11082
Key : Analysis.Init.CPU.mSec
Value: 327
Key : Analysis.Init.Elapsed.mSec
Value: 10642
Key : Analysis.Memory.CommitPeak.Mb
Value: 73
Key : WER.OS.Branch
Value: vb_release
Key : WER.OS.Timestamp
Value: 2019-12-06T14:06:00Z
Key : WER.OS.Version
Value: 10.0.19041.1
BUGCHECK_CODE: 3b
BUGCHECK_P1: c0000005
BUGCHECK_P2: fffff80266412849
BUGCHECK_P3: fffffc063d4e5cc0
BUGCHECK_P4: 0
CONTEXT: fffffc063d4e5cc0 -- (.cxr 0xfffffc063d4e5cc0)
rax=0000000000000001 rbx=000002000000aa30 rcx=000002000000aa30
rdx=0000000000000000 rsi=ffffbb02418942b0 rdi=00000000000004ac
rip=fffff80266412849 rsp=fffffc063d4e66c0 rbp=ffffe484b173a080
r8=0000000000000000 r9=0000000000000001 r10=00000000001f0003
r11=ffffbb02447d4c80 r12=fffffc063d4e6a58 r13=0000000000000000
r14=ffffbb024275a5c0 r15=fffffc063d4e6788
iopl=0 nv up ei ng nz na po nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00050286
nt!ObpIncrPointerCount+0x9:
fffff802`66412849 f0480fc101 lock xadd qword ptr [rcx],rax ds:002b:00000200`0000aa30=????????????????
Resetting default scope
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: WerFault.exe
STACK_TEXT:
fffffc06`3d4e66c0 fffff802`667e872a : ffffe484`b230a080 fffff802`667e9cc7 e484b2b9`a9300001 00000000`001f0003 : nt!ObpIncrPointerCount+0x9
fffffc06`3d4e6700 fffff802`667e97e4 : ffffe484`af8ec340 ffffe484`b230a080 fffffc06`3d4e6840 00000000`001fffff : nt!ObpReferenceProcessObjectByHandle+0xfa
fffffc06`3d4e6740 fffff802`667e82ec : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!ObDuplicateObject+0x144
fffffc06`3d4e6a00 fffff802`666085b8 : ffffe484`b173a080 000000a8`9556ea58 fffffc06`3d4e6aa8 00000000`00000000 : nt!NtDuplicateObject+0x10c
fffffc06`3d4e6a90 00007ffc`e2ced5a4 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x28
000000a8`9556ea38 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x00007ffc`e2ced5a4
SYMBOL_NAME: nt!ObpIncrPointerCount+9
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
IMAGE_VERSION: 10.0.19041.1081
STACK_COMMAND: .cxr 0xfffffc063d4e5cc0 ; kb
BUCKET_ID_FUNC_OFFSET: 9
FAILURE_BUCKET_ID: 0x3B_c0000005_nt!ObpIncrPointerCount
OS_VERSION: 10.0.19041.1
BUILDLAB_STR: vb_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {e8e6c0f9-dbe9-22d1-9f3f-fb54f1d8758a}
Followup: MachineOwner
---------