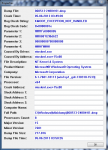
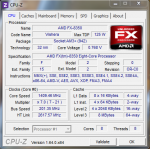
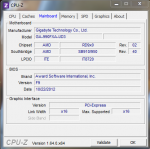
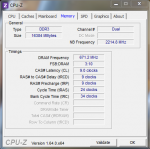
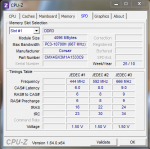
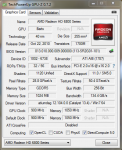
KMODE_EXCEPTION_NOT_HANDLED (1e)
This is a very common bugcheck. Usually the exception address pinpoints
the driver/function that caused the problem. Always note this address
as well as the link date of the driver/image that contains this address.
Arguments:
Arg1: ffffffffc0000005, The exception code that was not handled
Arg2: fffff80002f0d622, The address that the exception occurred at
Arg3: 0000000000000000, Parameter 0 of the exception
Arg4: ffffffffffffffff, Parameter 1 of the exception
Debugging Details:
------------------
TRIAGER: Could not open triage file : e:\dump_analysis\program\triage\modclass.ini, error 2
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - The instruction at "0x%08lx" referenced memory at "0x%08lx". The memory could not be "%s".
FAULTING_IP:
nt!KxWaitForLockOwnerShip+12
fffff800`02f0d622 48890a mov qword ptr [rdx],rcx
EXCEPTION_PARAMETER1: 0000000000000000
EXCEPTION_PARAMETER2: ffffffffffffffff
READ_ADDRESS: GetPointerFromAddress: unable to read from fffff80003114100
GetUlongFromAddress: unable to read from fffff800031141c0
ffffffffffffffff
ERROR_CODE: (NTSTATUS) 0xc0000005 - The instruction at "0x%08lx" referenced memory at "0x%08lx". The memory could not be "%s".
BUGCHECK_STR: 0x1e_c0000005
DEFAULT_BUCKET_ID: WIN7_DRIVER_FAULT
PROCESS_NAME: CCC.exe
CURRENT_IRQL: 2
LAST_CONTROL_TRANSFER: from fffff80002f27728 to fffff80002edcc00
CONTEXT: 6d941d85c3ff0004 -- (.cxr 0x6d941d85c3ff0004)
Unable to read context, Win32 error 0n30
STACK_TEXT:
fffff880`09bebcc8 fffff800`02f27728 : 00000000`0000001e ffffffff`c0000005 fffff800`02f0d622 00000000`00000000 : nt!KeBugCheckEx
fffff880`09bebcd0 fffff800`02edc282 : fffff880`09bec4a8 fffff800`031172e0 fffff880`09bec550 fffff880`02f65180 : nt! ?? ::FNODOBFM::`string'+0x487ed
fffff880`09bec370 fffff800`02edab8a : fffff800`03117bc0 00000000`00000000 00000000`00000000 00001f80`00000200 : nt!KiExceptionDispatch+0xc2
fffff880`09bec550 fffff800`02f0d622 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiGeneralProtectionFault+0x10a
fffff880`09bec6e0 fffff800`02ee5c5e : fffff800`031172e0 00000000`00000000 00000000`00000000 fffffa80`0b8050c0 : nt!KxWaitForLockOwnerShip+0x12
fffff880`09bec710 fffff800`02eed4c6 : fffffa80`0b4e1210 fffffa80`0b7efa90 fffff800`031172c0 fffff683`ff801e50 : nt!KeAcquireInStackQueuedSpinLockAtDpcLevel+0x7e
fffff880`09bec760 fffff800`02f0d06b : fffffa80`0b7efa90 fffffa80`0e8433f8 00000000`00000000 00000000`00000000 : nt!MiUnlinkPageFromLockedList+0x266
fffff880`09bec7e0 fffff800`02ef9c8f : 00000000`00000000 00000000`00000000 fffff800`02ee6a95 fffffa80`0e8433f8 : nt!MiResolveTransitionFault+0x16b
fffff880`09bec870 fffff800`02ee9179 : 00000000`2747d1f8 ffffffff`ffffffff fffffa80`0eb94060 fffff800`02edfc8f : nt!MiDispatchFault+0x95f
fffff880`09bec980 fffff800`02edad2e : 00000000`00000008 000007ff`00176390 00000000`0288ec01 00000000`03562e68 : nt!MmAccessFault+0x359
fffff880`09becae0 000007ff`00176390 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiPageFault+0x16e
00000000`2747d778 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x7ff`00176390
FOLLOWUP_IP:
nt!KxWaitForLockOwnerShip+12
fffff800`02f0d622 48890a mov qword ptr [rdx],rcx
SYMBOL_STACK_INDEX: 4
SYMBOL_NAME: nt!KxWaitForLockOwnerShip+12
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
DEBUG_FLR_IMAGE_TIMESTAMP: 5147d9c6
STACK_COMMAND: .cxr 0x6d941d85c3ff0004 ; kb
FAILURE_BUCKET_ID: X64_0x1e_c0000005_nt!KxWaitForLockOwnerShip+12
BUCKET_ID: X64_0x1e_c0000005_nt!KxWaitForLockOwnerShip+12