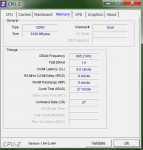
So, habe die Grafikkarte um 200Mhz runtergetaktet und eben kam mal wieder ein Bluescreen. Ich habe leider keine Möglichkeit, mir ein NT auszuleihen... Als nächstes werde ich die Spannung des Ram runtersetzen, wenn keine anderen Lösungsvorschläge kommen?!
Microsoft (R) Windows Debugger Version 6.2.9200.20512 X86
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\091013-14601-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*C:\symbols*
http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 7601.18205.amd64fre.win7sp1_gdr.130708-1532
Machine Name:
Kernel base = 0xfffff800`0304d000 PsLoadedModuleList = 0xfffff800`032906d0
Debug session time: Tue Sep 10 16:01:22.136 2013 (UTC + 2:00)
System Uptime: 0 days 1:33:52.385
Loading Kernel Symbols
.
Press ctrl-c (cdb, kd, ntsd) or ctrl-break (windbg) to abort symbol loads that take too long.
Run !sym noisy before .reload to track down problems loading symbols.
..............................................................
................................................................
..........................
Loading User Symbols
Loading unloaded module list
.....
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck 3B, {c0000005, 804003, fffff880088ecdc0, 0}
Probably caused by : ntkrnlmp.exe ( nt!KiSystemServiceHandler+7c )
Followup: MachineOwner
---------
1: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
SYSTEM_SERVICE_EXCEPTION (3b)
An exception happened while executing a system service routine.
Arguments:
Arg1: 00000000c0000005, Exception code that caused the bugcheck
Arg2: 0000000000804003, Address of the instruction which caused the bugcheck
Arg3: fffff880088ecdc0, Address of the context record for the exception that caused the bugcheck
Arg4: 0000000000000000, zero.
Debugging Details:
------------------
EXCEPTION_CODE: (NTSTATUS) 0xc0000005 - Die Anweisung in 0x%08lx verweist auf Speicher 0x%08lx. Der Vorgang %s konnte nicht im Speicher durchgef hrt werden.
FAULTING_IP:
+0
00000000`00804003 ?? ???
CONTEXT: fffff880088ecdc0 -- (.cxr 0xfffff880088ecdc0)
rax=0000000000000001 rbx=0000000000000001 rcx=fffff880088ed748
rdx=fffff900c0200228 rsi=fffff900c0216650 rdi=0000000000000000
rip=0000000000804003 rsp=fffff880088ed7a8 rbp=0000000000000001
r8=0000000000000000 r9=0000000000000017 r10=fffff880088ed690
r11=fffff900c0082d80 r12=fffff900c0800b90 r13=0000000000000000
r14=0000000000804003 r15=fffff900c0800b90
iopl=0 nv up ei ng nz na pe nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00010282
00000000`00804003 ?? ???
Resetting default scope
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN7_DRIVER_FAULT
BUGCHECK_STR: 0x3B
PROCESS_NAME: MSIAfterburner
CURRENT_IRQL: 0
LAST_CONTROL_TRANSFER: from 0000000000000000 to 0000000000804003
STACK_TEXT:
fffff880`088ec4f8 fffff800`030c2129 : 00000000`0000003b 00000000`c0000005 00000000`00804003 fffff880`088ecdc0 : nt!KeBugCheckEx
fffff880`088ec500 fffff800`030c1a7c : fffff880`088ed568 fffff880`088ecdc0 00000000`00000000 fffff960`003440d0 : nt!KiBugCheckDispatch+0x69
fffff880`088ec640 fffff800`030ed75d : fffff880`02d8408c fffff880`02d48814 fffff880`02ca1000 fffff880`088ed568 : nt!KiSystemServiceHandler+0x7c
fffff880`088ec680 fffff800`030ec535 : fffff800`032126c4 fffff880`088ec6f8 fffff880`088ed568 fffff800`0304d000 : nt!RtlpExecuteHandlerForException+0xd
fffff880`088ec6b0 fffff800`030fd4e1 : fffff880`088ed568 fffff880`088ecdc0 fffff880`00000000 00000000`00000000 : nt!RtlDispatchException+0x415
fffff880`088ecd90 fffff800`030c2202 : fffff880`088ed568 00000000`00000001 fffff880`088ed610 fffff900`c0216650 : nt!KiDispatchException+0x135
fffff880`088ed430 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiExceptionDispatch+0xc2
STACK_COMMAND: kb
FOLLOWUP_IP:
nt!KiSystemServiceHandler+7c
fffff800`030c1a7c b801000000 mov eax,1
SYMBOL_STACK_INDEX: 2
SYMBOL_NAME: nt!KiSystemServiceHandler+7c
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
DEBUG_FLR_IMAGE_TIMESTAMP: 51db806a
FAILURE_BUCKET_ID: X64_0x3B_nt!KiSystemServiceHandler+7c
BUCKET_ID: X64_0x3B_nt!KiSystemServiceHandler+7c
Followup: MachineOwner
---------