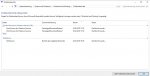
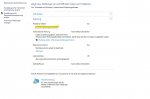
Also habe gerade meine Minidump ausgelesen mit dem Programm und es steht folgendes drin:
"
Microsoft (R) Windows Debugger Version 10.0.17763.1 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\020819-27968-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
* Path validation summary
**
Response Time (ms) Location
Deferred SRV
C:\Temphttp://msdl.microsoft.com/download/symbols
Symbol search path is: SRV
C:\Temphttp://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 10 Kernel Version 17763 MP (8 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Machine Name:
Kernel base = 0xfffff800
156b6000 PsLoadedModuleList = 0xfffff80015ad0a50
Debug session time: Fri Feb 8 00:43:48.901 2019 (UTC + 1:00)
System Uptime: 0 days 0:00:12.719
Loading Kernel Symbols
...............................................................
................................................................
Loading User Symbols
Loading unloaded module list
...
***
***
Use !analyze -v to get detailed debugging information.
BugCheck 1000007F, {8, fffff80017a6fe70, 1ff, fffff80015755b44}
Probably caused by : memory_corruption
Followup: memory_corruption
---------
0: kd> !analyze -v
***
***
UNEXPECTED_KERNEL_MODE_TRAP_M (1000007f)
This means a trap occurred in kernel mode, and it's a trap of a kind
that the kernel isn't allowed to have/catch (bound trap) or that
is always instant death (double fault). The first number in the
bugcheck params is the number of the trap (8 = double fault, etc)
Consult an Intel x86 family manual to learn more about what these
traps are. Here is a
portion of those codes:
If kv shows a taskGate
use .tss on the part before the colon, then kv.
Else if kv shows a trapframe
use .trap on that value
Else
.trap on the appropriate frame will show where the trap was taken
(on x86, this will be the ebp that goes with the procedure KiTrap)
Endif
kb will then show the corrected stack.
Arguments:
Arg1: 0000000000000008, EXCEPTION_DOUBLE_FAULT
Arg2: fffff80017a6fe70
Arg3: 00000000000001ff
Arg4: fffff80015755b44
Debugging Details:
------------------
KEY_VALUES_STRING: 1
STACKHASH_ANALYSIS: 1
TIMELINE_ANALYSIS: 1
DUMP_CLASS: 1
DUMP_QUALIFIER: 400
BUILD_VERSION_STRING: 10.0.17763.253 (WinBuild.160101.0800)
DUMP_FILE_ATTRIBUTES: 0x8
Kernel Generated Triage Dump
DUMP_TYPE: 2
BUGCHECK_P1: 8
BUGCHECK_P2: fffff80017a6fe70
BUGCHECK_P3: 1ff
BUGCHECK_P4: fffff80015755b44
BUGCHECK_STR: 0x7f_8
BAD_STACK_POINTER: 00000000000001ff
CPU_COUNT: 8
CPU_MHZ: dbc
CPU_VENDOR: AuthenticAMD
CPU_FAMILY: 15
CPU_MODEL: 2
CPU_STEPPING: 0
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: CODE_CORRUPTION
PROCESS_NAME: System
CURRENT_IRQL: 2
ANALYSIS_SESSION_HOST: DESKTOP-E0KQRQ7
ANALYSIS_SESSION_TIME: 02-08-2019 01:02:18.0126
ANALYSIS_VERSION: 10.0.17763.1 amd64fre
UNALIGNED_STACK_POINTER: 00000000000001ff
LAST_CONTROL_TRANSFER: from 0000000000000000 to fffff80015755b44
STACK_TEXT:
00000000
000001ff 0000000000000000 : 00000000
00000000 0000000000000000 00000000
00000000 0000000000000000 : nt!RtlpHpSegLfhVsCommit+0x64
CHKIMG_EXTENSION: !chkimg -lo 50 -d !nt
fffff80015755b22 - nt!RtlpHpSegLfhVsCommit+42
[ 41:40 ]
1 error : !nt (fffff80015755b22)
MODULE_NAME: memory_corruption
IMAGE_NAME: memory_corruption
FOLLOWUP_NAME: memory_corruption
DEBUG_FLR_IMAGE_TIMESTAMP: 0
MEMORY_CORRUPTOR: ONE_BIT
STACK_COMMAND: .thread ; .cxr ; kb
FAILURE_BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
BUCKET_ID: MEMORY_CORRUPTION_ONE_BIT
PRIMARY_PROBLEM_CLASS: MEMORY_CORRUPTION_ONE_BIT
TARGET_TIME: 2019-02-07T23:43:48.000Z
OSBUILD: 17763
OSSERVICEPACK: 253
SERVICEPACK_NUMBER: 0
OS_REVISION: 0
SUITE_MASK: 272
PRODUCT_TYPE: 1
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
OSEDITION: Windows 10 WinNt TerminalServer SingleUserTS
OS_LOCALE:
USER_LCID: 0
OSBUILD_TIMESTAMP: unknown_date
BUILDDATESTAMP_STR: 160101.0800
BUILDLAB_STR: WinBuild
BUILDOSVER_STR: 10.0.17763.253
ANALYSIS_SESSION_ELAPSED_TIME: 21ab
ANALYSIS_SOURCE: KM
FAILURE_ID_HASH_STRING: km:memory_corruption_one_bit
FAILURE_ID_HASH: {e3faf315-c3d0-81db-819a-6c43d23c63a7}"
... ich hoffe jemand kann mir das entschlüsseln^^
 Kernel Power bedeutet nichts anderes als, dass Windows unerwartet beendet/neugestartet wurde. Nur weil da Power drin steht heißt es doch nicht, dass es das Netzteil ist.
Kernel Power bedeutet nichts anderes als, dass Windows unerwartet beendet/neugestartet wurde. Nur weil da Power drin steht heißt es doch nicht, dass es das Netzteil ist.