Crash Dump Analysis provided by OSR Open Systems Resources, Inc. (
http://www.osr.com)
Online Crash Dump Analysis Service
See
http://www.osronline.com for more information
Windows 8 Kernel Version 17763 MP (16 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Machine Name:
Kernel base = 0xfffff801`02ca7000 PsLoadedModuleList = 0xfffff801`030c1a50
Debug session time: Sat Jan 26 15:34:53.317 2019 (UTC - 5:00)
System Uptime: 0 days 6:08:10.023
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: ffffc58446124e38, memory referenced
Arg2: 00000000000000ff, IRQL
Arg3: 0000000000000000, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff80102da00b4, address which referenced memory
Debugging Details:
------------------
TRIAGER: Could not open triage file : e:\dump_analysis\program\triage\modclass.ini, error 2
READ_ADDRESS: unable to get nt!MmSpecialPoolStart
unable to get nt!MmSpecialPoolEnd
unable to get nt!MmPagedPoolEnd
unable to get nt!MmNonPagedPoolStart
unable to get nt!MmSizeOfNonPagedPoolInBytes
ffffc58446124e38
CURRENT_IRQL: 0
FAULTING_IP:
nt!ExpApplyPriorityBoost+304
fffff801`02da00b4 f0480fb199488d4dc8 lock cmpxchg qword ptr [rcx-37B272B8h],rbx
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: WIN8_DRIVER_FAULT
BUGCHECK_STR: AV
PROCESS_NAME: csrss.exe
BAD_PAGES_DETECTED: f41f
TRAP_FRAME: fffffa02a71cb150 -- (.trap 0xfffffa02a71cb150)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=fffffa02a71cb320 rbx=0000000000000000 rcx=ffffc5847dc4c0f0
rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80102da00b4 rsp=fffffa02a71cb2e0 rbp=fffffa02a71cb358
r8=0000000000000004 r9=ffffc584889f5080 r10=ffffc5847f635080
r11=ffffb28aa8441ac0 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up di pl zr na po nc
nt!ExpApplyPriorityBoost+0x304:
fffff801`02da00b4 f0480fb199488d4dc8 lock cmpxchg qword ptr [rcx-37B272B8h],rbx ds:ffffc584`46124e38=????????????????
Resetting default scope
LAST_CONTROL_TRANSFER: from fffff80102e6a369 to fffff80102e58b40
STACK_TEXT:
fffffa02`a71cb008 fffff801`02e6a369 : 00000000`0000000a ffffc584`46124e38 00000000`000000ff 00000000`00000000 : nt!KeBugCheckEx
fffffa02`a71cb010 fffff801`02e6678e : 00000000`00000000 00000000`00000000 00000000`00000000 fffff801`0332b02f : nt!KiBugCheckDispatch+0x69
fffffa02`a71cb150 fffff801`02da00b4 : ffffc584`8573d720 ffffc584`7dc4c090 ffff66e2`00000000 fffffa02`a71cbb00 : nt!KiPageFault+0x44e
fffffa02`a71cb2e0 fffff801`02dc14d5 : 00000000`00000000 fffffeb3`00000002 ffffc584`7dc4c0f0 fffffed6`c06c4900 : nt!ExpApplyPriorityBoost+0x304
fffffa02`a71cb380 fffff801`02dc073f : 00000000`00000002 00000000`000000f0 fffffeb3`00000000 00000171`00000377 : nt!ExpAcquireResourceExclusiveLite+0x335
fffffa02`a71cb450 fffffeb3`ae931588 : ffffc584`7de09cd0 00000000`00989680 00000000`00000001 00000000`00000000 : nt!ExEnterCriticalRegionAndAcquireResourceExclusive+0x3f
fffffa02`a71cb490 fffffeb3`addee900 : 00000000`00000000 fffffa02`a71cb679 00000000`00000000 fffffeb3`ae9a7b3a : win32kbase!EnterCrit+0x88
fffffa02`a71cb570 fffffeb3`ae9a7baa : 00000000`00000051 00000000`00000000 fffffa02`a71cb5d0 00000000`00000000 : win32kfull!EnterEditionCrit+0x30
fffffa02`a71cb5a0 fffffeb3`ae9a59ef : ffffc584`7cfb5c20 00000000`00000000 fffffed6`c06062d0 00000000`00000003 : win32kbase!ApiSetEditionCrit::ApiSetEditionCrit+0x36
fffffa02`a71cb5d0 fffffeb3`ae997c95 : fffffed6`c06062d0 fffffed6`c06062d0 fffffed6`c06062d0 ffffc584`7ce19070 : win32kbase!RIMReadInput+0x9f
fffffa02`a71cb6c0 fffffeb3`aea5fd93 : 00000000`00000000 00000000`00000000 fffffed6`c06062d0 fffffed6`00000000 : win32kbase!CBaseInput::Read+0x55
fffffa02`a71cb710 fffffeb3`ae912d97 : 00000000`00000040 00000000`00000000 00000000`00000003 fffffed6`c06062d0 : win32kbase!CBaseInput::OnReadNotification+0x1f3
fffffa02`a71cb790 fffffeb3`ae912ae2 : 00000000`00000000 fffffed6`c06e3830 fffffa02`a71cb9e9 00000000`00000002 : win32kbase!CBaseInput::OnDispatcherObjectSignaled+0x1df
fffffa02`a71cb830 fffffeb3`ae99cf8c : 00000000`00000000 00000000`00000000 fffffeb3`aeae5a01 fffffed6`c06e3830 : win32kbase!CBaseInput::_OnDispatcherObjectSignaled+0x12
fffffa02`a71cb860 fffffeb3`ae99ce26 : 00000000`00000004 fffffed6`c06e3830 00000000`00000004 fffffed6`0000000d : win32kbase!LegacyInputDispatcher:

ispatch+0x88
fffffa02`a71cb890 fffffeb3`add86ce6 : fffffed6`c06a9050 fffffed6`c06a9050 00000000`00000002 00000000`00000002 : win32kbase!LegacyInputDispatcher::WaitAndDispatch+0xb6
fffffa02`a71cb910 fffffeb3`add86a24 : 00000000`00000000 00000000`00000000 00000000`00000000 fffffeb3`aeae5ad0 : win32kfull!xxxDesktopThreadWaiter+0x12a
fffffa02`a71cb990 fffffeb3`ae94b025 : ffffc584`7f635080 ffffc584`7f635080 00000000`00000000 00000000`00000005 : win32kfull!xxxDesktopThread+0x354
fffffa02`a71cba50 fffffeb3`addaf230 : ffffc584`7f635080 fffffa02`a71cbb80 00000000`00000000 00000000`00000000 : win32kbase!xxxCreateSystemThreads+0x155
fffffa02`a71cbad0 fffff801`02e69d85 : ffffc584`7f635080 00000000`00000005 000001b2`118043e0 00000000`0000044c : win32kfull!NtUserCallNoParam+0x70
fffffa02`a71cbb00 00007fff`d1901144 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x25
00000009`800bfa28 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x7fff`d1901144
STACK_COMMAND: kb
SYMBOL_NAME: PAGE_NOT_ZERO
FOLLOWUP_NAME: MachineOwner
MODULE_NAME: Unknown_Module
IMAGE_NAME: Unknown_Image
DEBUG_FLR_IMAGE_TIMESTAMP: 0
BUCKET_ID: PAGE_NOT_ZERO
Followup: MachineOwner
---------
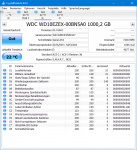
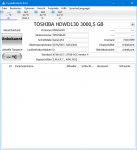
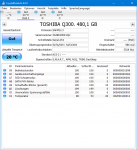
*** Memory manager detected 62495 instance(s) of page corruption, target is likely to have memory corruption.