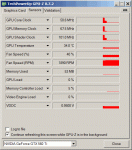
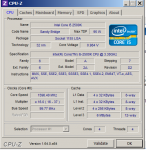
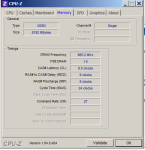
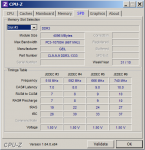
Hallo!
Ich bin neu hier und ich habe das gleiche,oder zumendist ein ähnliches, Problem, welches am Anfang geschildert wurde. Zudem ist mein PC meiner Meinung nach von einem auf den anderen Tag extrem langsam geworden. Malwarescanner und ähnliches hab ich schon versucht. Ihr seid meine letzte Hoffnung

Ich habe den Debugger bei beiden dumps durchlaufen lassen und folgendes ist dabei herausgekommen.
Microsoft (R) Windows Debugger Version 6.2.9200.20512 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\073113-18314-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*C:\symbols*
http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 7601.18113.amd64fre.win7sp1_gdr.130318-1533
Machine Name:
Kernel base = 0xfffff800`0301f000 PsLoadedModuleList = 0xfffff800`03262670
Debug session time: Wed Jul 31 22:35:35.355 2013 (UTC + 2:00)
System Uptime: 0 days 0:49:22.759
Loading Kernel Symbols
...............................................................
................................................................
................
Loading User Symbols
Loading unloaded module list
.....
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck C4, {62, fffffa8009151ae8, fffffa8009147c30, 1}
*** WARNING: Unable to verify timestamp for mbam.sys
*** ERROR: Module load completed but symbols could not be loaded for mbam.sys
Probably caused by : mbam.sys
Followup: MachineOwner
---------
3: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
DRIVER_VERIFIER_DETECTED_VIOLATION (c4)
A device driver attempting to corrupt the system has been caught. This is
because the driver was specified in the registry as being suspect (by the
administrator) and the kernel has enabled substantial checking of this driver.
If the driver attempts to corrupt the system, bugchecks 0xC4, 0xC1 and 0xA will
be among the most commonly seen crashes.
Arguments:
Arg1: 0000000000000062, A driver has forgotten to free its pool allocations prior to unloading.
Arg2: fffffa8009151ae8, name of the driver having the issue.
Arg3: fffffa8009147c30, verifier internal structure with driver information.
Arg4: 0000000000000001, total # of (paged+nonpaged) allocations that weren't freed.
Type !verifier 3 drivername.sys for info on the allocations
that were leaked that caused the bugcheck.
Debugging Details:
------------------
BUGCHECK_STR: 0xc4_62
IMAGE_NAME: mbam.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 512fbf03
MODULE_NAME: mbam
FAULTING_MODULE: fffff88005d84000 mbam
VERIFIER_DRIVER_ENTRY: dt nt!_MI_VERIFIER_DRIVER_ENTRY fffffa8009147c30
Symbol nt!_MI_VERIFIER_DRIVER_ENTRY not found.
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VERIFIER_ENABLED_VISTA_MINIDUMP
PROCESS_NAME: services.exe
CURRENT_IRQL: 2
LAST_CONTROL_TRANSFER: from fffff800035224ec to fffff80003094c00
STACK_TEXT:
fffff880`07aa7308 fffff800`035224ec : 00000000`000000c4 00000000`00000062 fffffa80`09151ae8 fffffa80`09147c30 : nt!KeBugCheckEx
fffff880`07aa7310 fffff800`0353165a : 00000000`00000001 00000000`00000000 fffff880`05d84000 00000000`00000001 : nt!VerifierBugCheckIfAppropriate+0x3c
fffff880`07aa7350 fffff800`03187270 : 00000000`00000000 00000000`00000000 fffff880`02fd7180 00000000`00000000 : nt!VfPoolCheckForLeaks+0x4a
fffff880`07aa7390 fffff800`0344a7ee : fffffa80`09151a30 00000000`00000000 00000000`00000000 00000000`ffffffff : nt!VfTargetDriversRemove+0x160
fffff880`07aa7430 fffff800`0346f243 : 00000000`00000000 00000000`000e0082 00000000`00000000 00000000`00000001 : nt!VfDriverUnloadImage+0x2e
fffff880`07aa7460 fffff800`0346f6bd : 00000000`00000000 fffffa80`09151a30 00000000`00000000 00000000`00010200 : nt!MiUnloadSystemImage+0x283
fffff880`07aa74d0 fffff800`03510c51 : 00000000`00000000 fffff880`07aa77f0 fffffa80`069ff210 00000000`00000018 : nt!MmUnloadSystemImage+0x4d
fffff880`07aa7510 fffff800`0309de44 : 00000000`00000000 fffff880`07aa77f0 fffffa80`069ff210 fffffa80`09153b38 : nt!IopDeleteDriver+0x41
fffff880`07aa7540 fffff800`03480f5e : fffff880`07aa77f0 00000000`00000000 00000000`c0000001 fffff800`00000000 : nt!ObfDereferenceObject+0xd4
fffff880`07aa75a0 fffff800`03093e93 : fffffa80`08bee660 fffff880`07aa77c0 00000000`00000001 fffff980`6db0a000 : nt!IopUnloadDriver+0x45c
fffff880`07aa7770 fffff800`03090450 : fffff800`03480c57 00000000`019fe7a0 00000000`00000001 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
fffff880`07aa7908 fffff800`03480c57 : 00000000`019fe7a0 00000000`00000001 00000000`00000000 00000000`00cfe680 : nt!KiServiceLinkage
fffff880`07aa7910 fffff800`03093e93 : fffffa80`08bee660 fffff880`07aa7b60 00000000`00000000 00000000`00000000 : nt!IopUnloadDriver+0x155
fffff880`07aa7ae0 00000000`77272b8a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`019fe778 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x77272b8a
STACK_COMMAND: kb
FOLLOWUP_NAME: MachineOwner
FAILURE_BUCKET_ID: X64_0xc4_62_VRF_LEAKED_POOL_IMAGE_mbam.sys
BUCKET_ID: X64_0xc4_62_VRF_LEAKED_POOL_IMAGE_mbam.sys
Followup: MachineOwner
---------
3: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
DRIVER_VERIFIER_DETECTED_VIOLATION (c4)
A device driver attempting to corrupt the system has been caught. This is
because the driver was specified in the registry as being suspect (by the
administrator) and the kernel has enabled substantial checking of this driver.
If the driver attempts to corrupt the system, bugchecks 0xC4, 0xC1 and 0xA will
be among the most commonly seen crashes.
Arguments:
Arg1: 0000000000000062, A driver has forgotten to free its pool allocations prior to unloading.
Arg2: fffffa8009151ae8, name of the driver having the issue.
Arg3: fffffa8009147c30, verifier internal structure with driver information.
Arg4: 0000000000000001, total # of (paged+nonpaged) allocations that weren't freed.
Type !verifier 3 drivername.sys for info on the allocations
that were leaked that caused the bugcheck.
Debugging Details:
------------------
BUGCHECK_STR: 0xc4_62
IMAGE_NAME: mbam.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 512fbf03
MODULE_NAME: mbam
FAULTING_MODULE: fffff88005d84000 mbam
VERIFIER_DRIVER_ENTRY: dt nt!_MI_VERIFIER_DRIVER_ENTRY fffffa8009147c30
Symbol nt!_MI_VERIFIER_DRIVER_ENTRY not found.
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VERIFIER_ENABLED_VISTA_MINIDUMP
PROCESS_NAME: services.exe
CURRENT_IRQL: 2
LAST_CONTROL_TRANSFER: from fffff800035224ec to fffff80003094c00
STACK_TEXT:
fffff880`07aa7308 fffff800`035224ec : 00000000`000000c4 00000000`00000062 fffffa80`09151ae8 fffffa80`09147c30 : nt!KeBugCheckEx
fffff880`07aa7310 fffff800`0353165a : 00000000`00000001 00000000`00000000 fffff880`05d84000 00000000`00000001 : nt!VerifierBugCheckIfAppropriate+0x3c
fffff880`07aa7350 fffff800`03187270 : 00000000`00000000 00000000`00000000 fffff880`02fd7180 00000000`00000000 : nt!VfPoolCheckForLeaks+0x4a
fffff880`07aa7390 fffff800`0344a7ee : fffffa80`09151a30 00000000`00000000 00000000`00000000 00000000`ffffffff : nt!VfTargetDriversRemove+0x160
fffff880`07aa7430 fffff800`0346f243 : 00000000`00000000 00000000`000e0082 00000000`00000000 00000000`00000001 : nt!VfDriverUnloadImage+0x2e
fffff880`07aa7460 fffff800`0346f6bd : 00000000`00000000 fffffa80`09151a30 00000000`00000000 00000000`00010200 : nt!MiUnloadSystemImage+0x283
fffff880`07aa74d0 fffff800`03510c51 : 00000000`00000000 fffff880`07aa77f0 fffffa80`069ff210 00000000`00000018 : nt!MmUnloadSystemImage+0x4d
fffff880`07aa7510 fffff800`0309de44 : 00000000`00000000 fffff880`07aa77f0 fffffa80`069ff210 fffffa80`09153b38 : nt!IopDeleteDriver+0x41
fffff880`07aa7540 fffff800`03480f5e : fffff880`07aa77f0 00000000`00000000 00000000`c0000001 fffff800`00000000 : nt!ObfDereferenceObject+0xd4
fffff880`07aa75a0 fffff800`03093e93 : fffffa80`08bee660 fffff880`07aa77c0 00000000`00000001 fffff980`6db0a000 : nt!IopUnloadDriver+0x45c
fffff880`07aa7770 fffff800`03090450 : fffff800`03480c57 00000000`019fe7a0 00000000`00000001 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
fffff880`07aa7908 fffff800`03480c57 : 00000000`019fe7a0 00000000`00000001 00000000`00000000 00000000`00cfe680 : nt!KiServiceLinkage
fffff880`07aa7910 fffff800`03093e93 : fffffa80`08bee660 fffff880`07aa7b60 00000000`00000000 00000000`00000000 : nt!IopUnloadDriver+0x155
fffff880`07aa7ae0 00000000`77272b8a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`019fe778 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x77272b8a
STACK_COMMAND: kb
FOLLOWUP_NAME: MachineOwner
FAILURE_BUCKET_ID: X64_0xc4_62_VRF_LEAKED_POOL_IMAGE_mbam.sys
BUCKET_ID: X64_0xc4_62_VRF_LEAKED_POOL_IMAGE_mbam.sys
Followup: MachineOwner
---------
Und hier der zweite Durchlauf:
Microsoft (R) Windows Debugger Version 6.2.9200.20512 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\073113-21949-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: SRV*C:\symbols*
http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 7 Kernel Version 7601 (Service Pack 1) MP (4 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS Personal
Built by: 7601.18113.amd64fre.win7sp1_gdr.130318-1533
Machine Name:
Kernel base = 0xfffff800`0301b000 PsLoadedModuleList = 0xfffff800`0325e670
Debug session time: Wed Jul 31 21:43:19.250 2013 (UTC + 2:00)
System Uptime: 0 days 0:05:08.670
Loading Kernel Symbols
...............................................................
................................................................
.................
Loading User Symbols
Loading unloaded module list
....
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Use !analyze -v to get detailed debugging information.
BugCheck C4, {62, fffffa80092b0fe8, fffffa80093a64c0, 1}
*** WARNING: Unable to verify timestamp for mbam.sys
*** ERROR: Module load completed but symbols could not be loaded for mbam.sys
Probably caused by : mbam.sys
Followup: MachineOwner
---------
3: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
DRIVER_VERIFIER_DETECTED_VIOLATION (c4)
A device driver attempting to corrupt the system has been caught. This is
because the driver was specified in the registry as being suspect (by the
administrator) and the kernel has enabled substantial checking of this driver.
If the driver attempts to corrupt the system, bugchecks 0xC4, 0xC1 and 0xA will
be among the most commonly seen crashes.
Arguments:
Arg1: 0000000000000062, A driver has forgotten to free its pool allocations prior to unloading.
Arg2: fffffa80092b0fe8, name of the driver having the issue.
Arg3: fffffa80093a64c0, verifier internal structure with driver information.
Arg4: 0000000000000001, total # of (paged+nonpaged) allocations that weren't freed.
Type !verifier 3 drivername.sys for info on the allocations
that were leaked that caused the bugcheck.
Debugging Details:
------------------
BUGCHECK_STR: 0xc4_62
IMAGE_NAME: mbam.sys
DEBUG_FLR_IMAGE_TIMESTAMP: 512fbf03
MODULE_NAME: mbam
FAULTING_MODULE: fffff88005dcb000 mbam
VERIFIER_DRIVER_ENTRY: dt nt!_MI_VERIFIER_DRIVER_ENTRY fffffa80093a64c0
Symbol nt!_MI_VERIFIER_DRIVER_ENTRY not found.
CUSTOMER_CRASH_COUNT: 1
DEFAULT_BUCKET_ID: VERIFIER_ENABLED_VISTA_MINIDUMP
PROCESS_NAME: services.exe
CURRENT_IRQL: 2
LAST_CONTROL_TRANSFER: from fffff8000351e4ec to fffff80003090c00
STACK_TEXT:
fffff880`0849b308 fffff800`0351e4ec : 00000000`000000c4 00000000`00000062 fffffa80`092b0fe8 fffffa80`093a64c0 : nt!KeBugCheckEx
fffff880`0849b310 fffff800`0352d65a : 00000000`00000001 00000000`00000000 fffff880`05dcb000 00000000`00000001 : nt!VerifierBugCheckIfAppropriate+0x3c
fffff880`0849b350 fffff800`03183270 : 00000000`00000000 00000000`00000000 fffff880`02fd7180 00000000`00000000 : nt!VfPoolCheckForLeaks+0x4a
fffff880`0849b390 fffff800`034467ee : fffffa80`092b0f30 00000000`00000000 00000000`00000000 00000000`00000000 : nt!VfTargetDriversRemove+0x160
fffff880`0849b430 fffff800`0346b243 : 00000000`00000000 00000000`000e0082 00000000`00000000 00000000`00000001 : nt!VfDriverUnloadImage+0x2e
fffff880`0849b460 fffff800`0346b6bd : 00000000`00000000 fffffa80`092b0f30 00000000`00000000 00000000`00010200 : nt!MiUnloadSystemImage+0x283
fffff880`0849b4d0 fffff800`0350cc51 : 00000000`00000000 fffff880`0849b7f0 fffffa80`07438210 00000000`00000018 : nt!MmUnloadSystemImage+0x4d
fffff880`0849b510 fffff800`03099e44 : 00000000`00000000 fffff880`0849b7f0 fffffa80`07438210 fffffa80`0939f2f8 : nt!IopDeleteDriver+0x41
fffff880`0849b540 fffff800`0347cf5e : fffff880`0849b7f0 00000000`00000000 00000000`c0000001 fffff800`00000000 : nt!ObfDereferenceObject+0xd4
fffff880`0849b5a0 fffff800`0308fe93 : fffffa80`07c0eb50 fffff880`0849b7c0 00000000`00000001 fffff980`3bdbc000 : nt!IopUnloadDriver+0x45c
fffff880`0849b770 fffff800`0308c450 : fffff800`0347cc57 00000000`01d1e960 00000000`00000001 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
fffff880`0849b908 fffff800`0347cc57 : 00000000`01d1e960 00000000`00000001 00000000`00000000 00000000`00d4e680 : nt!KiServiceLinkage
fffff880`0849b910 fffff800`0308fe93 : fffffa80`07c0eb50 fffff880`0849bb60 00000000`00000000 00000000`00000000 : nt!IopUnloadDriver+0x155
fffff880`0849bae0 00000000`76f32b8a : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!KiSystemServiceCopyEnd+0x13
00000000`01d1e938 00000000`00000000 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : 0x76f32b8a
STACK_COMMAND: kb
FOLLOWUP_NAME: MachineOwner
FAILURE_BUCKET_ID: X64_0xc4_62_VRF_LEAKED_POOL_IMAGE_mbam.sys
BUCKET_ID: X64_0xc4_62_VRF_LEAKED_POOL_IMAGE_mbam.sys
Followup: MachineOwner
---------
Ich hoffe das ist in ordnung so. Ich wusste nicht wie man das als Datei abspeichert.
Für Antworten bin ich sehr dankbar.
Liebe Grüße
Kai